3 Easy Steps to 95% CVE Remediation One Unified Platform

Curated Images
RF Curated, Near Zero CVE Images
- Hardened NIST 800-70 images
- FIPS 140-3 validation
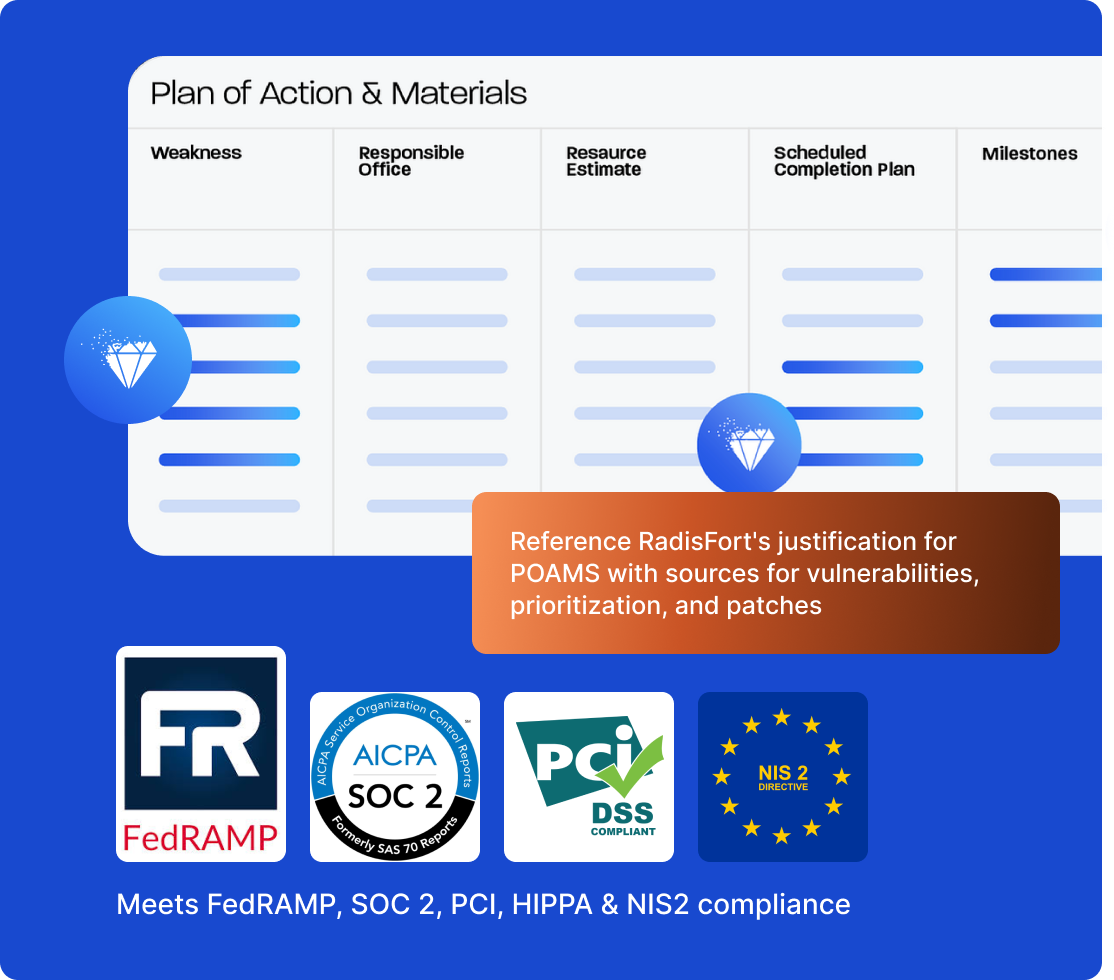
- RF Justification for POAMs
- Fresh images daily

Instrument & Profile
RF DevTime Protection Tools
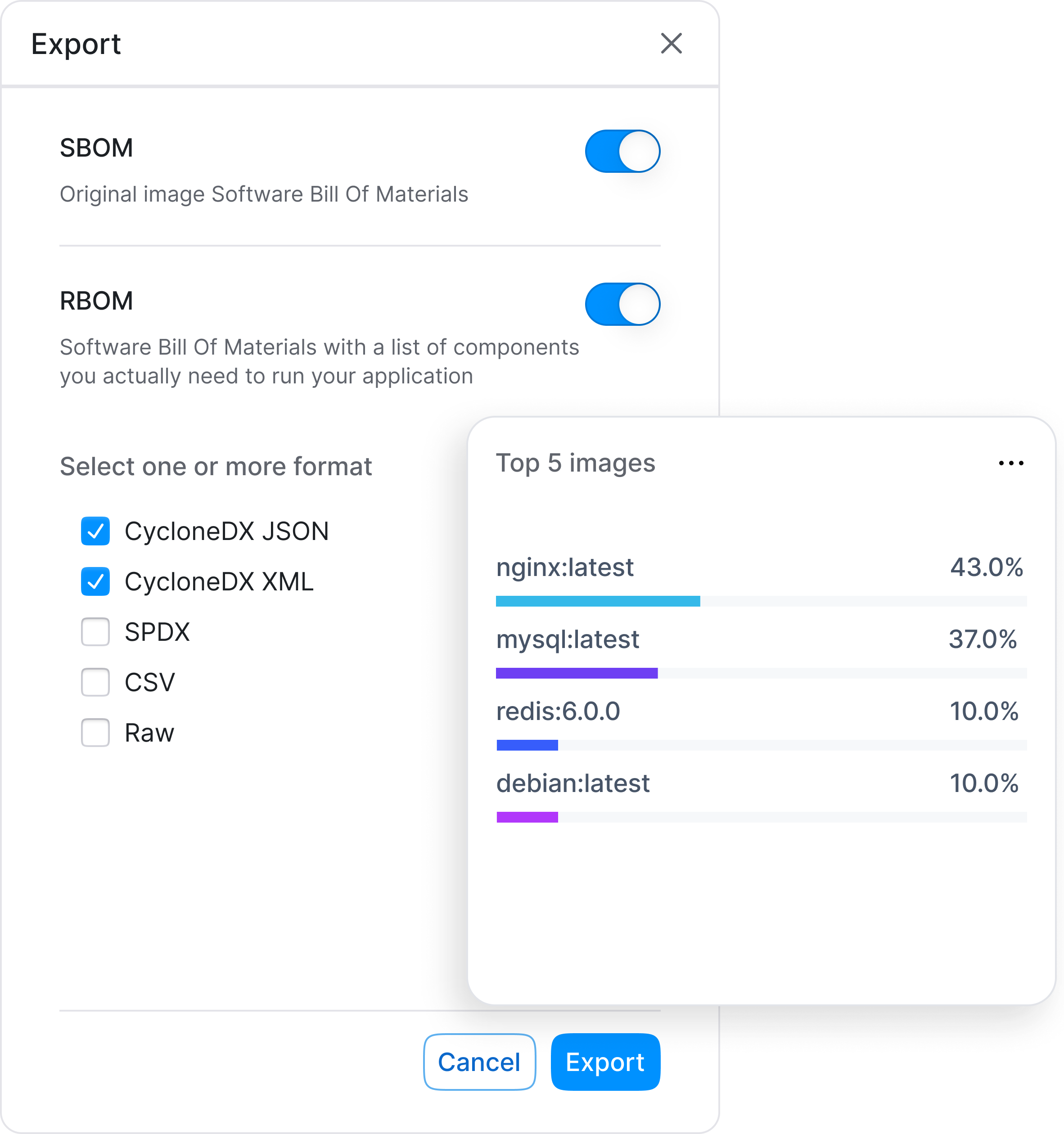
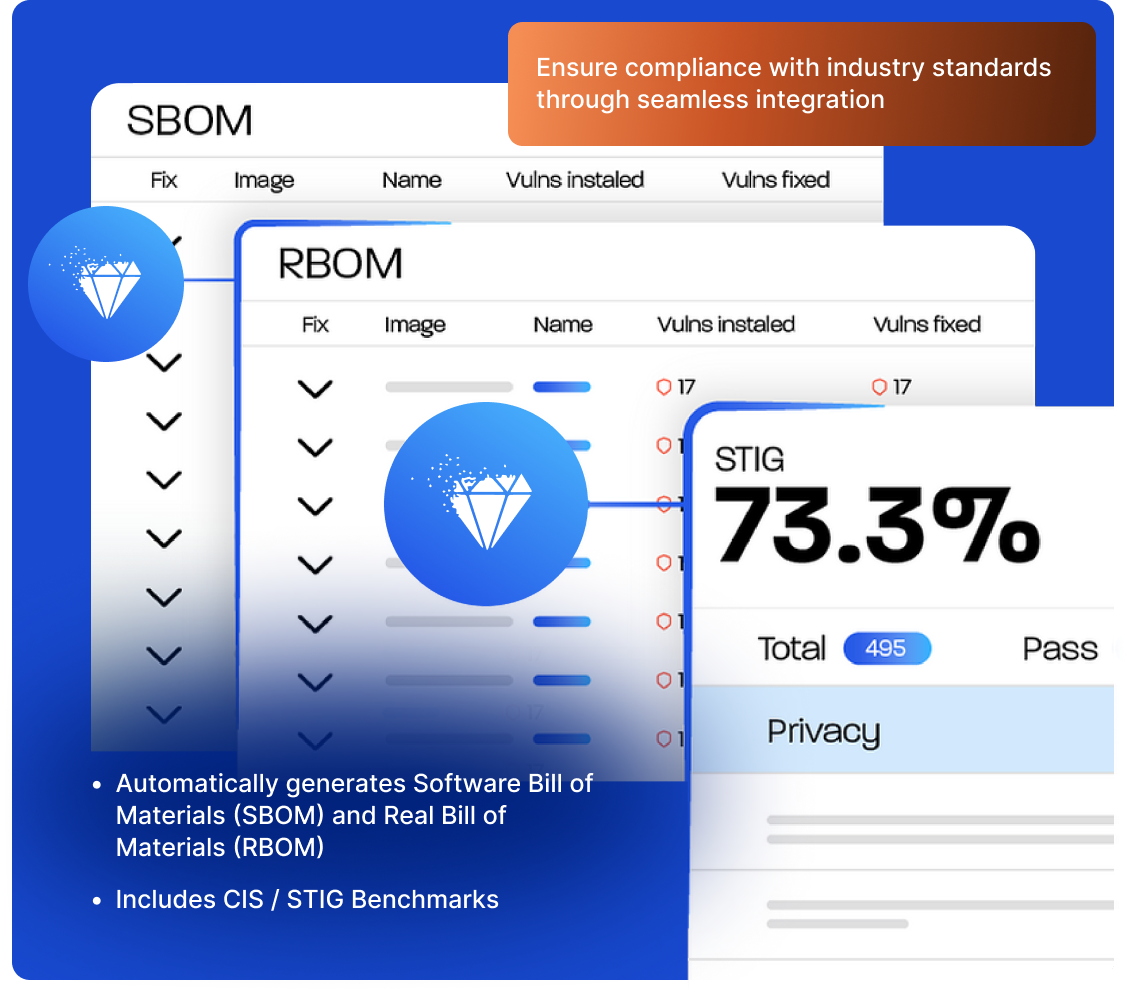
- Generate SBOM and RBOM
- Prioritize vulnerability remediation
- Integrated CIS / STIG Benchmarks
- Filter noise with RapidFort advisory

Harden & Defend
RF RunTime Protection Tools
- Secure unused components
- 90% Reduced software attack surface
- Boost software efficiency and security
- Consume less than 1% overhead
A secure foundation for software development and deployment
5.8M
vulnerabilities identified
4M
Million CVEs removed.
6M
Images downloaded
6000+
Largest library Near Zero CVE Images
170,000
Hardened container images made available.
Securing the Global Software Supply Chain
RapidFort Software Supply Chain Security Platform
The only platform that starts secure and stays secure — from base image to production runtime.
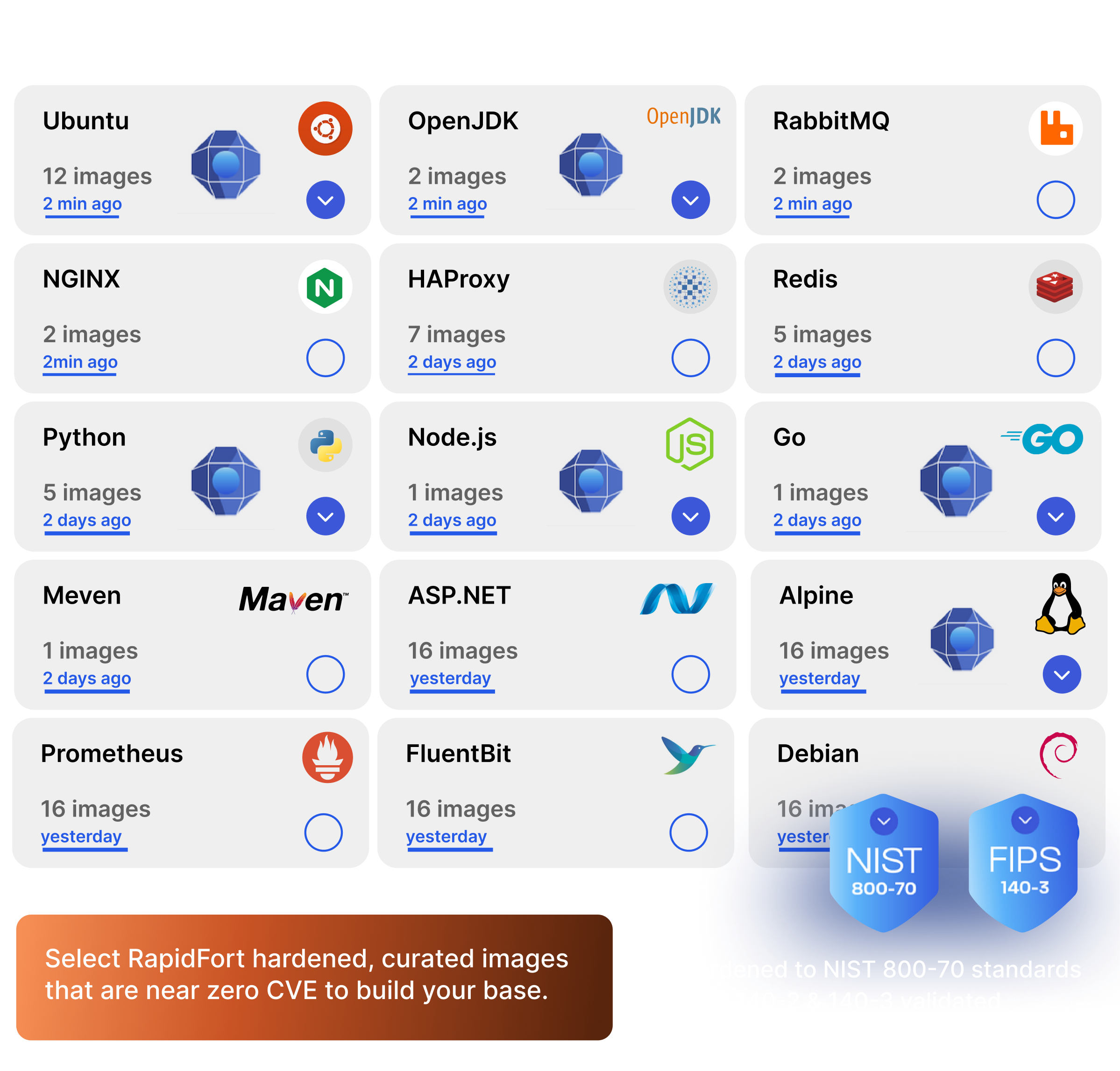
RF Curated Images
RapidFort provides curated container images with near zero CVEs. Our images offer a secure foundation for software development and deployment, with daily builds, FIPS readiness, for accelerated FedRAMP compliance.
Software Attack Surface Management
Continuously identify, profile, and harden software — from build to production.
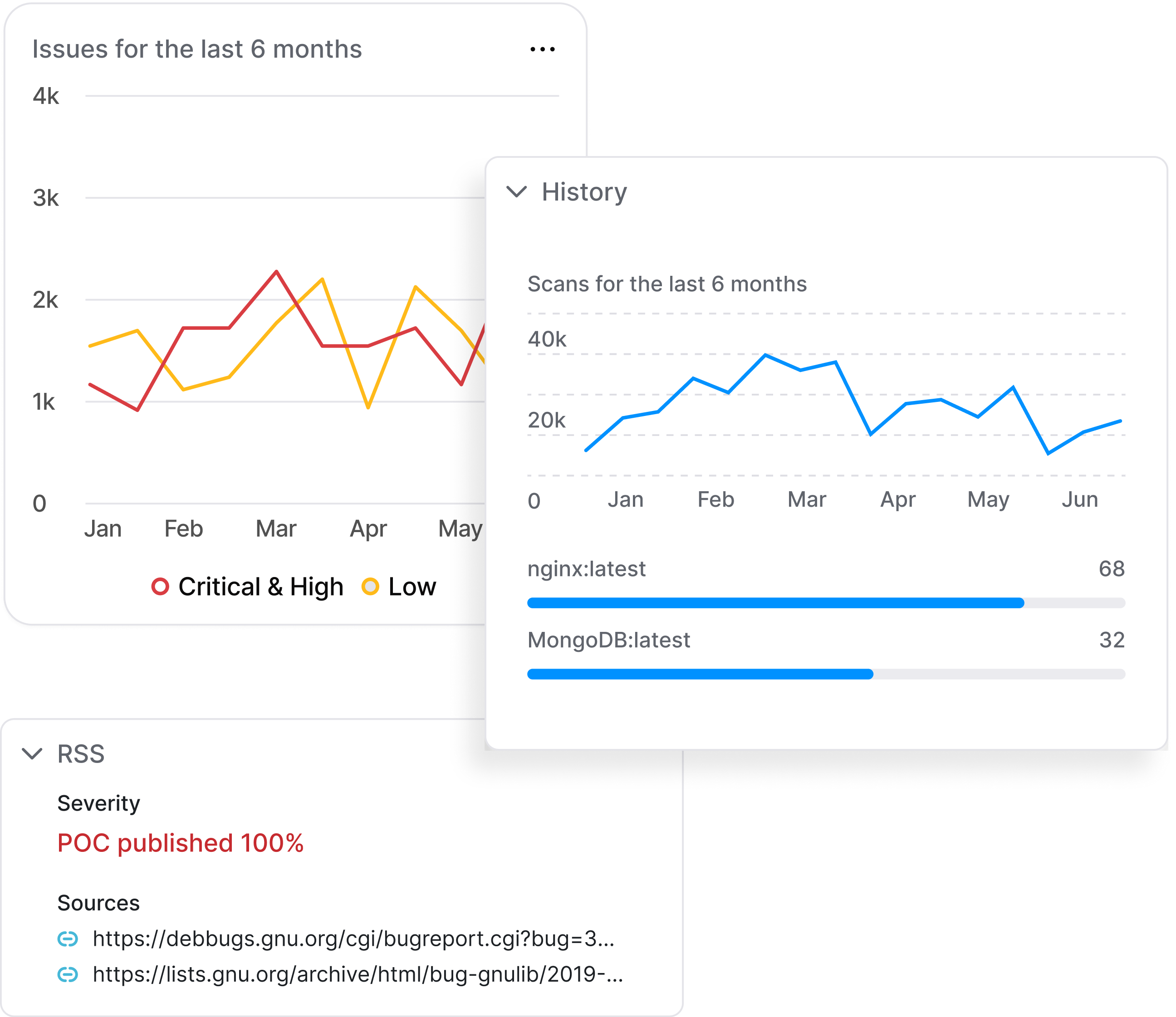
RF Image Scanner
Scan smarter with binary-level precision and execution-path awareness. RapidFort delivers fast, accurate CVE detection across registries, CI/CD, and Kubernetes — with minimal noise.
RF DevTime Protection
RapidFort’s DevTime tools instrument your containers during build and test to observe actual application behavior. They identify unused components, detect unreachable code paths, and generate an RBOM™ (Runtime Bill of Materials™) — giving teams actionable insights to reduce bloat, improve code quality, and prepare for secure runtime enforcement.
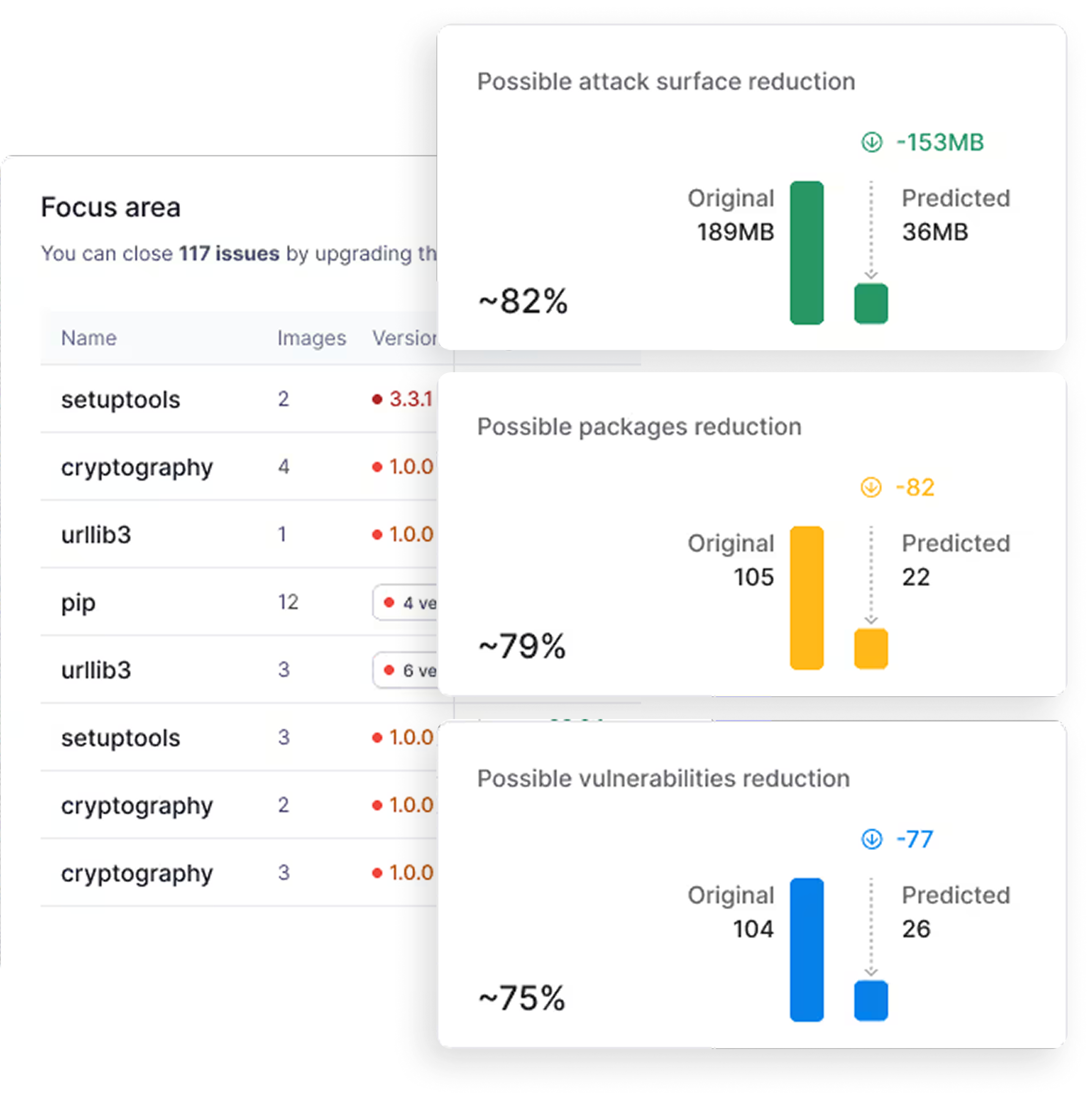
RF RunTime Protection
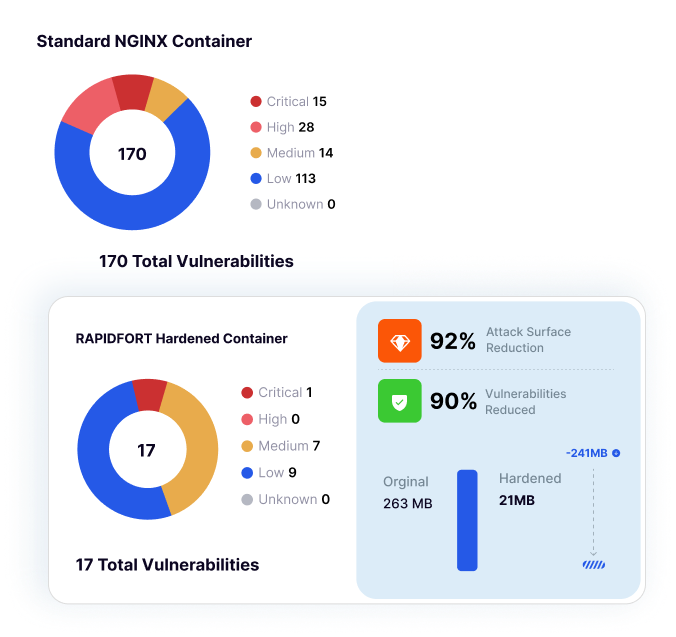
Stop wasting time on CVEs that don’t impact production. RapidFort’s RunTime protection monitors real execution, removes unused components, and reduces vulnerabilities by up to 95% and attack surface by 90% — with no code changes or developer disruption.


Secure by Design. Trusted by Federal and Enterprise Partners.
From containerized SaaS to classified infrastructure, RapidFort supports trusted vendors securing the software supply chain at scale.






















Integration
Integrate RapidFort directly into your existing workflows and tech stack


















See what our users think about Rapidfort
Use Cases
Understand how teams use RapidFort to secure applications.
Vulnerability Remediation
The current vulnerability remediation process is time-consuming and inefficient, and software releases are delayed. It involves hours of engineering time to identify and prioritize each vulnerability, research the root cause, and eventually fix each vulnerability before release.
RapidFort’s innovative solution automates Vulnerability Identification, reporting, prioritization, root-cause analysis, and remediation in just a few minutes.RapidFort remediates over 95% of vulnerabilities automatically with no code changes.
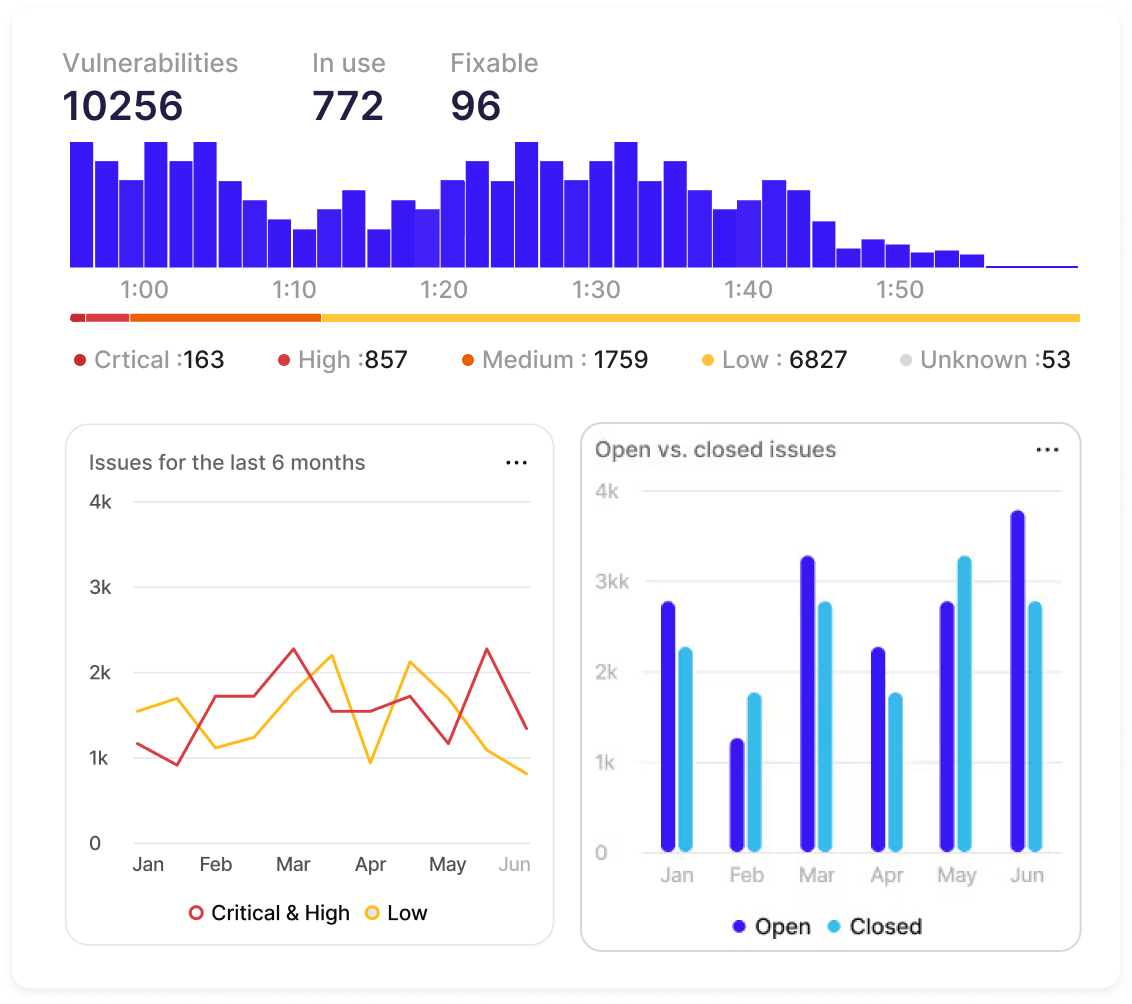
Software Supply Chain Security
Is it really a supply chain? Open source software is given to you as-is. Read the fine print. The less software you have, the less supply chain risk you have. Did you know 50-90% of the software you’re maintaining is just bloat? Let RapidFort identify and automatically secure the zombie code for you.
FedRAMP Compliance
Achieving FedRAMP compliance can be a complex and time-consuming process, but RapidFort simplifies and accelerates it with its advanced security optimization platform. By reducing vulnerabilities through its near-zero CVE container images, DevTime protection, and RunTime protection, RapidFort helps organizations build hardened cloud environments that align with FedRAMP’s stringent security controls. With automated security hardening, continuous monitoring, and detailed software bill of materials (SBOM) generation, RapidFort enables federal agencies and cloud service providers to streamline their compliance journey while strengthening overall security.
Frequently asked questions
Our team is here to support your RapidFort journey from day one. Here are some general FAQs to help you find what you need.
RapidFort achieves up to 95% CVE reduction by combining RF Near Zero CVE Images with the Software Attack Surface Management (SASM) platform. This includes Instrumentation and Profiling (DevTime) to identify unused components and generate Runtime Bill of Materials (RBOM™), followed by Hardening and Defending (RunTime) to remove non-executed code and remediate vulnerabilities based on actual execution paths — all without modifying source code.
The RapidFort Software Attack Surface Management (SASM) platform analyzes containerized applications during both build-time and run-time to identify and remove unused or unreachable components. It reduces the software attack surface, remediates vulnerabilities based on actual runtime execution, and continuously protects workloads post-deployment. SASM integrates seamlessly into CI/CD workflows and plays a central role in eliminating up to 95% of CVEs without requiring source code changes.
RF Near Zero CVE Images are pre-hardened container images with minimized footprints and near-zero known vulnerabilities. They are aligned to CIS and STIG benchmarks, validated for FIPS 140-3 compliance, and designed for regulated, production-grade deployments. These images help accelerate compliance readiness for frameworks such as FedRAMP, CMMC, SOC 2, PCI DSS, HIPAA, and NIS2.

Join our community and discuss your security needs with our technical advisors
Contact our technical security specialists for personalized assistance with your software security challenges. Or join our community on Slack to learn, connect, and collaborate.