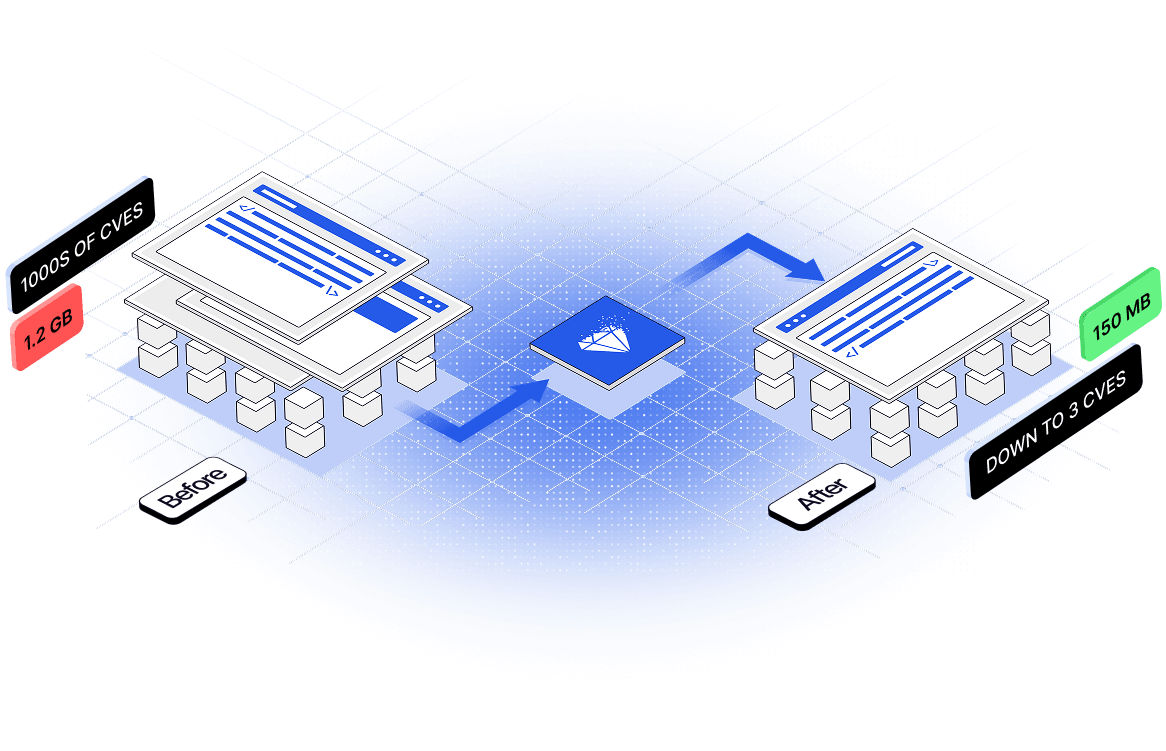
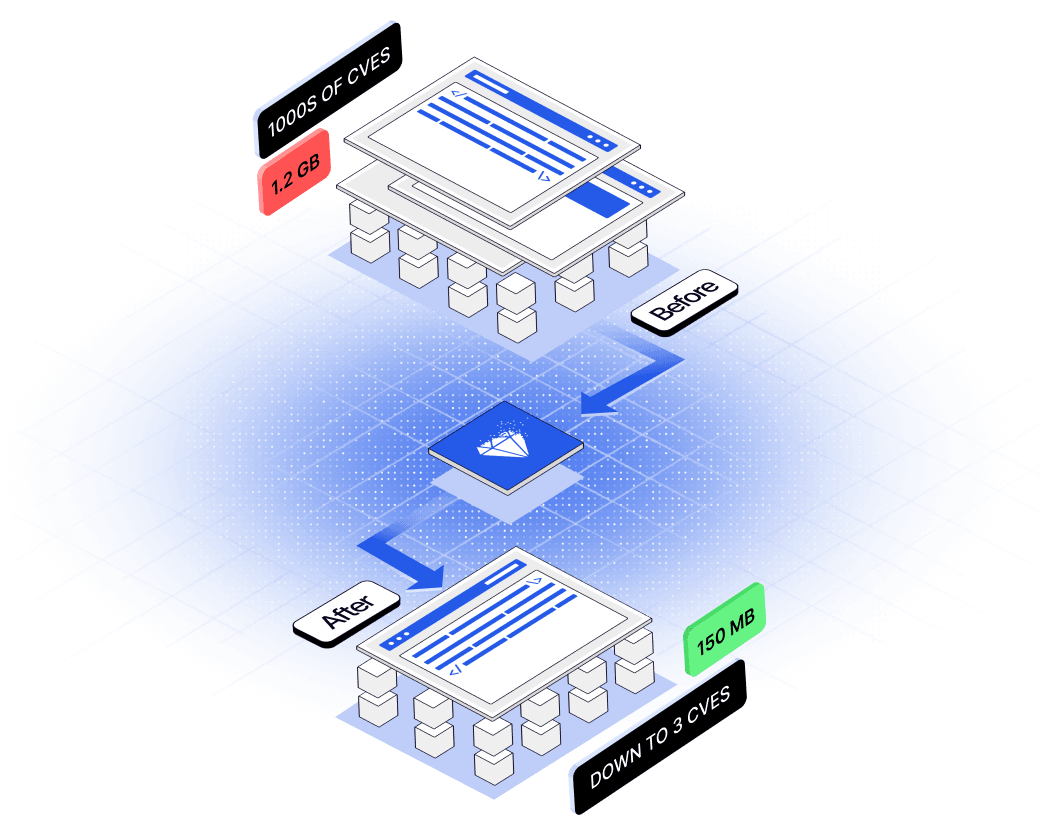
3 Easy Steps to 95% CVE Remediation One Unified Platform
Analyze & Profile CVEs
Replace with Clean Curated Images
Optimize & Harden
What Makes RapidFort the Smarter Choice
Faster Releases
Support for major LTS linux variants - Ubuntu, RHEL, Debian, Alpine - no vendor lock in to proprietary OS.
Complete End to End Platform
Complete Platform: Scanner, Benchmarking, Profiling, Hardening.
Full Stack optimization effectiveness
Allows end customer full stack software to be secured (3rd and 1st party software)
Benchmarking for Commercial and Federal
Has its own STIG/CIS integrated scanner
Patched vs daily build
RF images are patched with minimal code changes and robust software change management
Built to Eliminate Risk, Accelerate Compliance, and Reduce Costs
90%
Attack Surface Reduction
Remove dormant, unused, and unreachable components
100%
Real Execution Path Visibility
See exactly what runs - and what never should
82M
Packages Secured
Scanned, profiled, and monitored via DevTime and RunTime tools.
124 M
Vulnerabilities Removed
Eliminated through container hardening - no code changes required.
95%
CVE Remediation
Eliminate vulnerabilities automatically — without code changes
1M+
Images Hardened
Optimized Containers by reducing software attack surface
From CVE Chaos to Clarity: What Our Customers Are Saying
Securing the Global Software Supply Chain
RapidFort Software Supply Chain Security Platform
The only platform that starts secure and stays secure - from base image to production runtime.
Analyzer
Profiler
Curated Images
Optimizer
Cart
Vulnerability Analysis for Modern Containerized Software
RF Analyzer delivers validated, low-noise vulnerability intelligence by analyzing real image contents, configurations, and applicability context.
Understand What Actually Runs in Production
RF Profiler provides real-time runtime visibility into container behavior, exposing which components actually execute, so teams can focus on exploitable risks, not theoretical CVEs.

Remediate 95% of CVEs Automatically - no code or pipeline changes needed
Near Zero Vulnerability Images with FIPS validated modules

Runtime-Aware Container Hardening

Automated Compliance. Continuous Remediation. Complete Assurance.
RF CART continuously validates containers and virtual machines against approved security baselines and drives remediation with audit-ready evidence built in.

Use Cases
Understand how teams use RapidFort to secure applications.
Automated Vulnerability Remediation
The current vulnerability remediation process is time-consuming and inefficient, and software releases are delayed. It involves hours of engineering time to identify and prioritize each vulnerability, research the root cause, and eventually fix each vulnerability before release.
RapidFort’s innovative solution automates Vulnerability Identification, reporting, prioritization, root-cause analysis, and remediation in just a few minutes. RapidFort remediates over 95% of vulnerabilities automatically with no code changes.
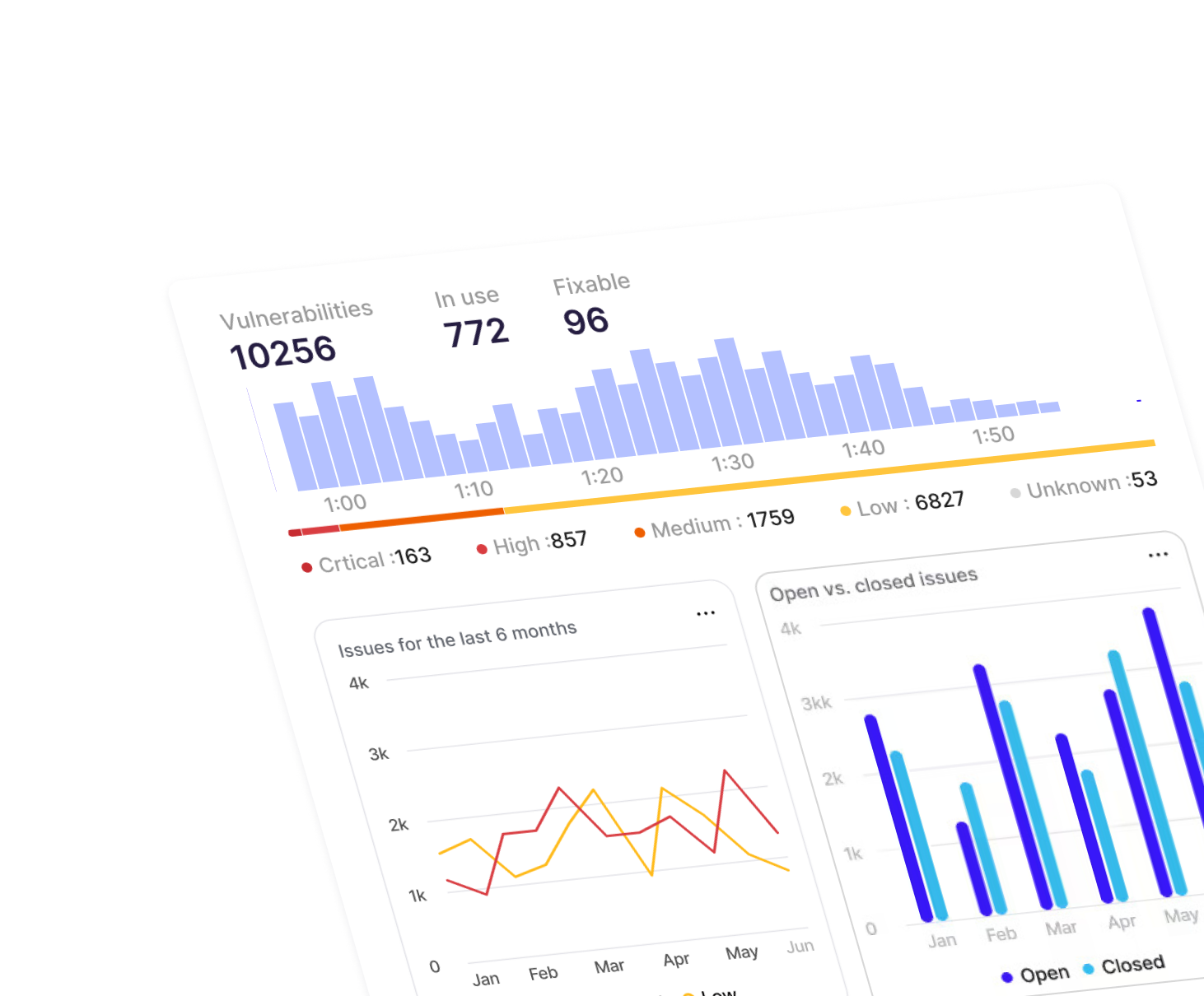
Secure Container Images
The current vulnerability remediation process is time-consuming and inefficient, and software releases are delayed. It involves hours of engineering time to identify and prioritize each vulnerability, research the root cause, and eventually fix each vulnerability before release.
RapidFort’s innovative solution automates Vulnerability Identification, reporting, prioritization, root-cause analysis, and remediation in just a few minutes. RapidFort remediates over 95% of vulnerabilities automatically with no code changes.

Software Attack Surface Management
The current vulnerability remediation process is time-consuming and inefficient, and software releases are delayed. It involves hours of engineering time to identify and prioritize each vulnerability, research the root cause, and eventually fix each vulnerability before release.
RapidFort’s innovative solution automates Vulnerability Identification, reporting, prioritization, root-cause analysis, and remediation in just a few minutes. RapidFort remediates over 95% of vulnerabilities automatically with no code changes.

Accelerate Compliance Readiness
The current vulnerability remediation process is time-consuming and inefficient, and software releases are delayed. It involves hours of engineering time to identify and prioritize each vulnerability, research the root cause, and eventually fix each vulnerability before release.
RapidFort’s innovative solution automates Vulnerability Identification, reporting, prioritization, root-cause analysis, and remediation in just a few minutes. RapidFort remediates over 95% of vulnerabilities automatically with no code changes.

Runtime Protection
The current vulnerability remediation process is time-consuming and inefficient, and software releases are delayed. It involves hours of engineering time to identify and prioritize each vulnerability, research the root cause, and eventually fix each vulnerability before release.
RapidFort’s innovative solution automates Vulnerability Identification, reporting, prioritization, root-cause analysis, and remediation in just a few minutes. RapidFort remediates over 95% of vulnerabilities automatically with no code changes.

Secure by Design. Trusted by Federal and Enterprise Partners.
From containerized SaaS to classified infrastructure, RapidFort supports trusted vendors securing the software supply chain at scale.






















Integrate RapidFort Directly Into Your Existing Workflows and Tech Stack
Frequently Asked Questions
Answers to Your Most Common Questions


RapidFort is a Software Supply Chain Security platform that helps teams identify, prioritize, and remediate software vulnerabilities - without code changes - by combining DevTime Protection Tools, Curated Near‑Zero CVE Images, and RunTime Protection Tools into a Software Attack Surface Management (SASM) workflow. Typical outcomes include up to 95% CVE remediation and up to 90% attack surface reduction driven by runtime intelligence.


Step 1 — Inventory & Understand (DevTime Protection Tools):
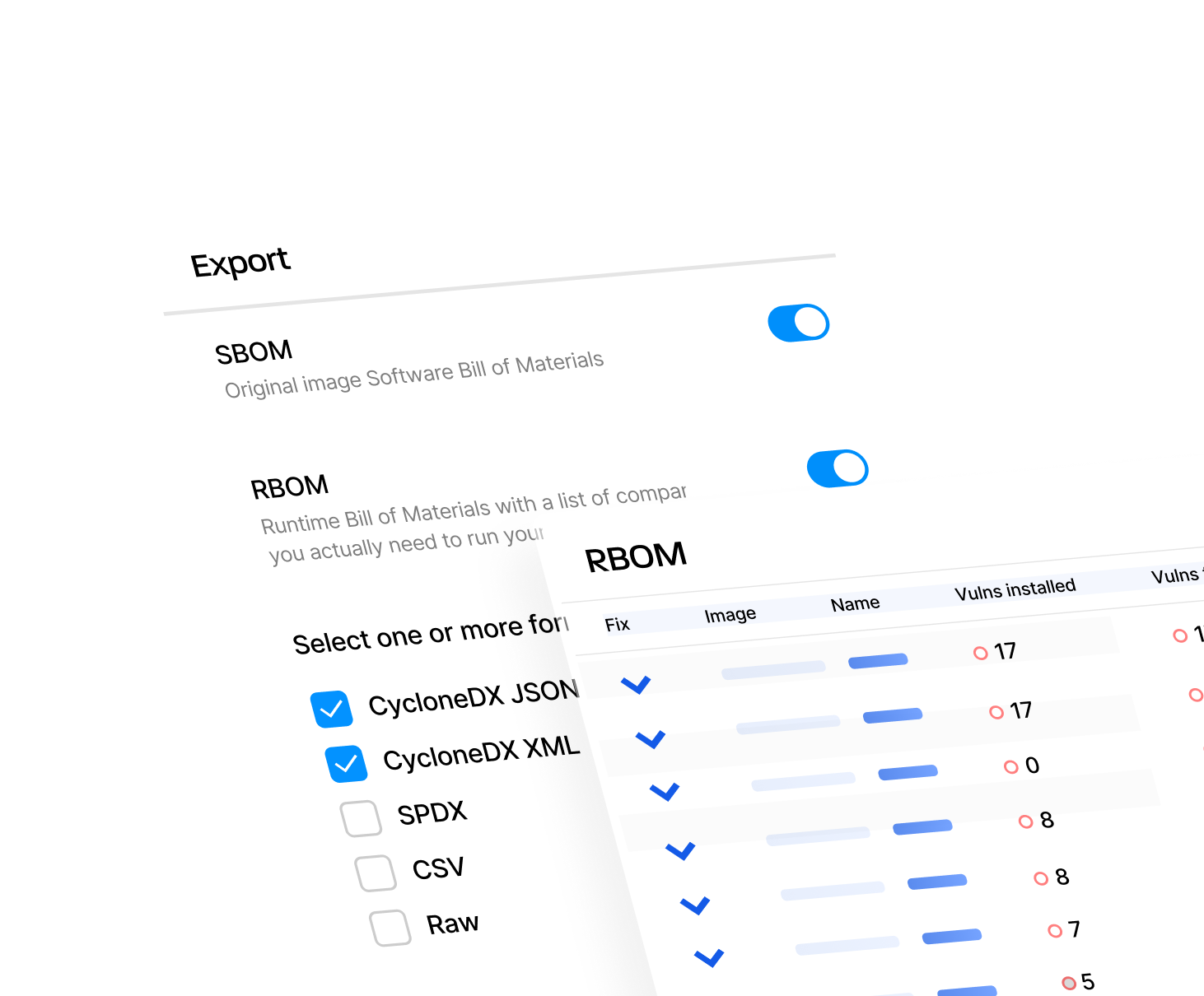
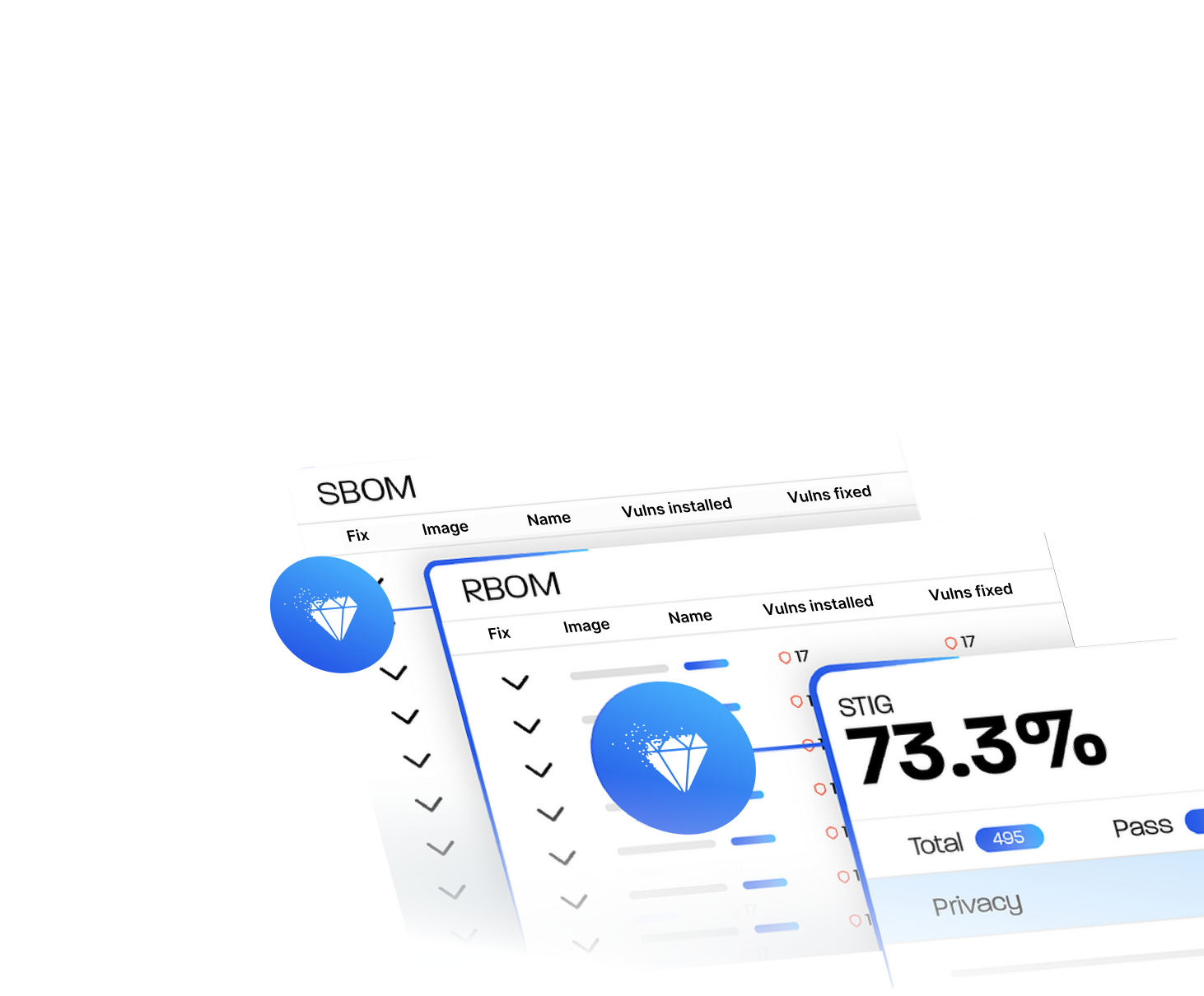
Integrate with your CI/CD pipeline or directly into your Kubernetes environment to scan container images, generate SBOM/RBOM™, reconcile scanner findings, detect drift, and profile execution paths using binary scanning. Outputs include SPDX/CycloneDX reports and RapidRisk Score to prioritize real risk.
Step 2 - Remediate & Automate (Curated Near‑Zero CVE Images):
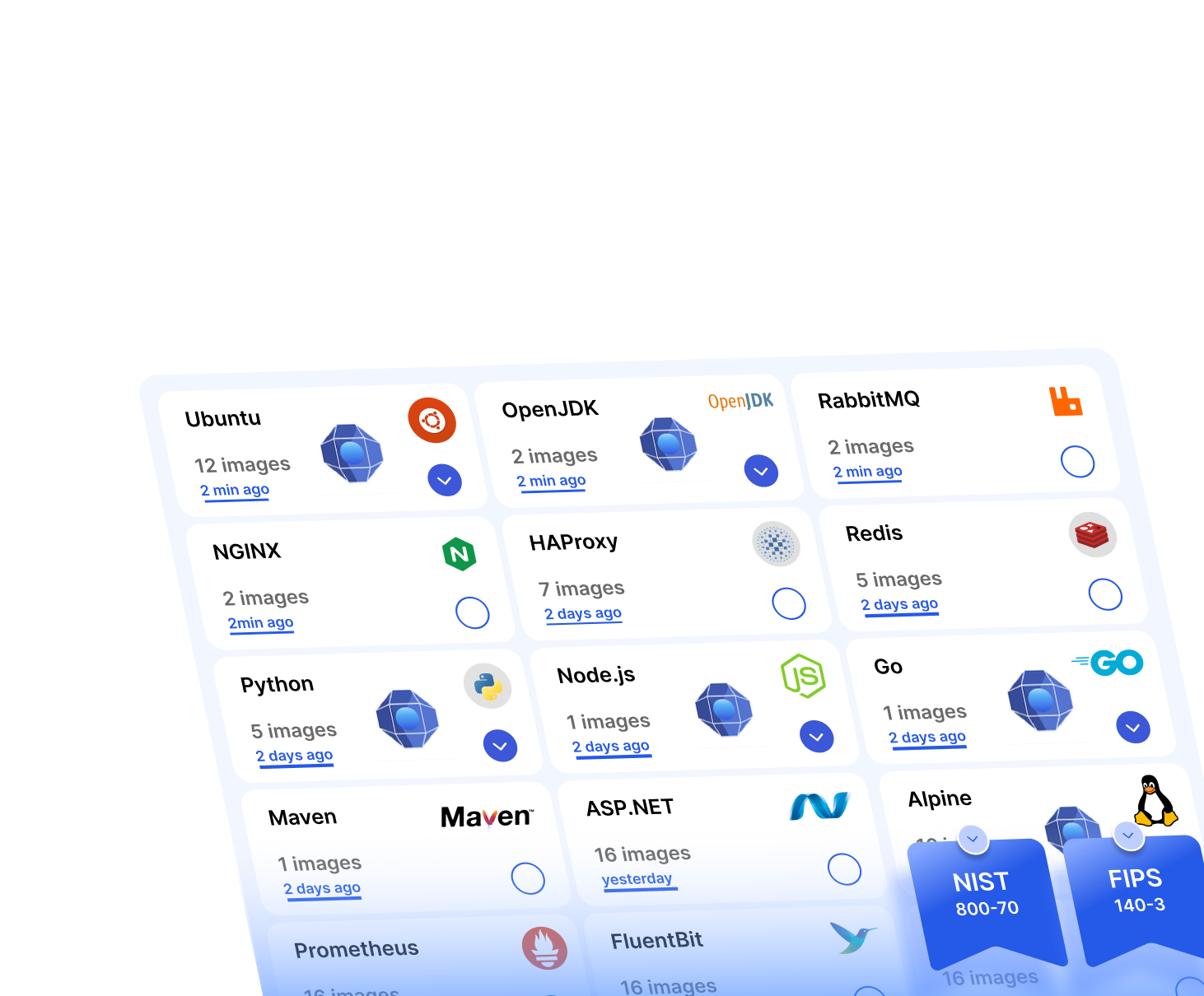
Drop‑in 10,000+ curated images built on LTS distributions (Alpine, Debian, Red Hat, Ubuntu), hardened with STIG/CIS in alignment with NIST SP 800‑70, with FIPS 140‑3 validation and continuous patching - so teams start with near zero CVEs. No vendor lock‑in.
Step 3 - Maintain & Defend (RunTime Protection Tools):
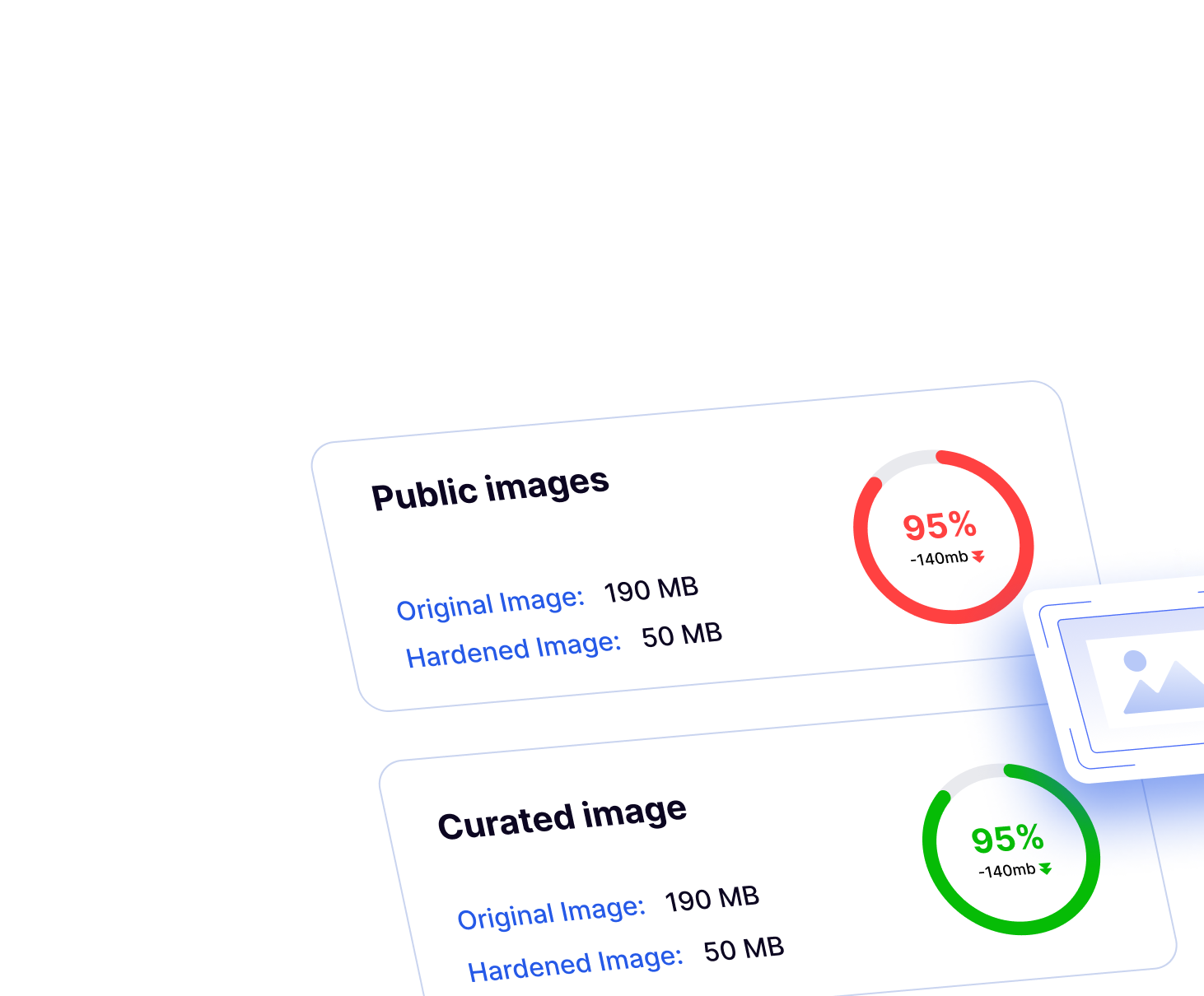
Enforces runtime‑guided hardening to remove unused components, continuously monitors baselines, and alerts on anomalies - achieving up to 95% CVE remediation and up to 90% attack surface reduction with <1% compute overhead.


They are production‑grade base images that are continuously patched and scanned, available across LTS Linux (Alpine, Debian, Red Hat, Ubuntu), hardened using STIG/CIS benchmarks (aligned to NIST SP 800‑70), and offered at scale (10,000+ images). They are designed to accelerate FedRAMP/CMMC/SOC 2 readiness and avoid lock‑in by using widely adopted distributions.