Most scanners inspect package metadata only and miss binaries, embedded tools, and custom artifacts inside images.
Reported vulnerabilities often lack applicability context, forcing teams to manually validate findings.
Distribution advisories inflate CVE counts even when affected packages are not present or reachable.
RF Analyzer replaces surface-level scanning with deep, validated analysis you can act on with confidence.
Enumerates all files, packages, and configurations within container images, not just those reported by package managers.
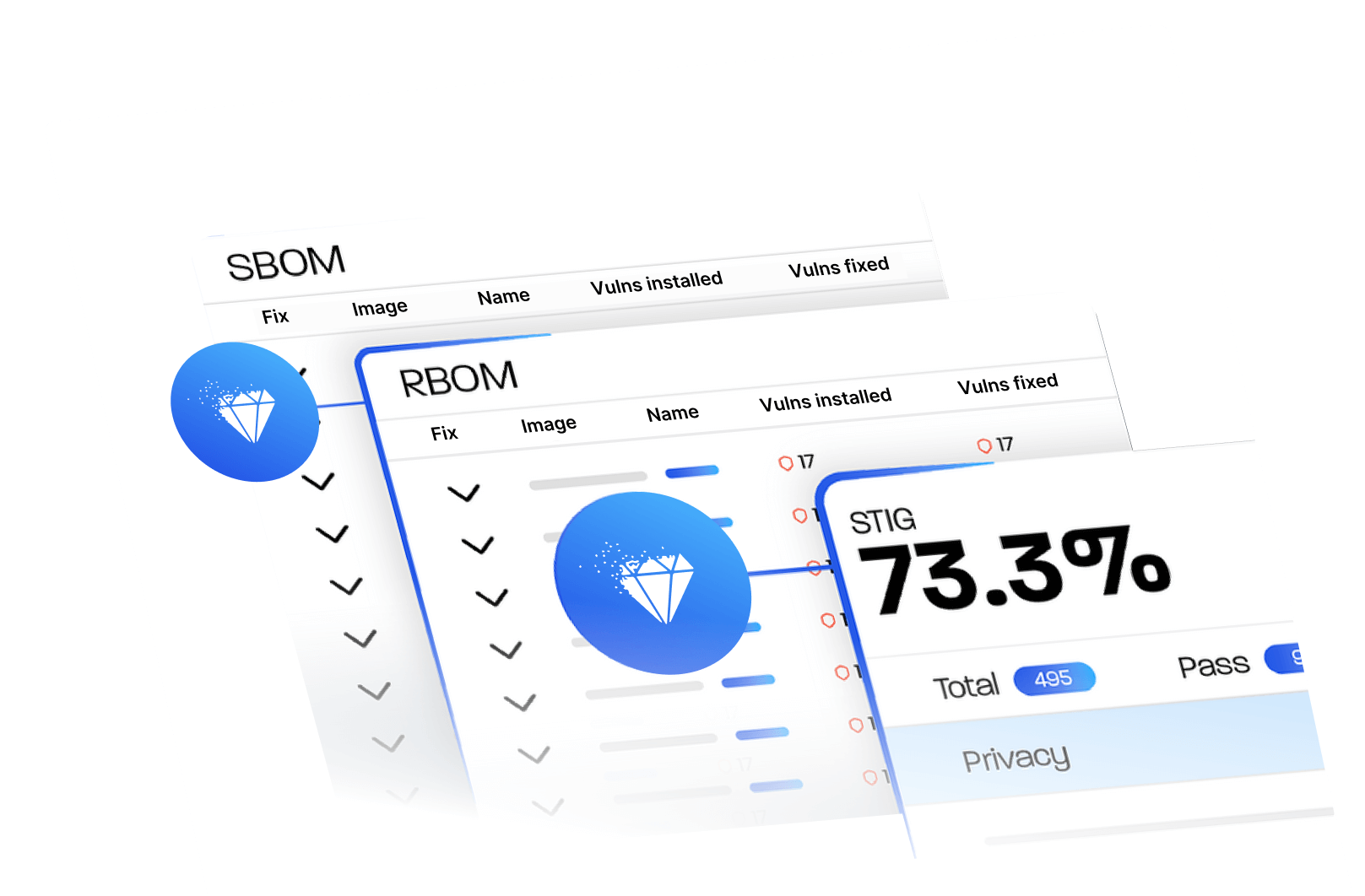
Confirms whether a vulnerability truly applies to the image by accounting for distribution specifics, package presence, and configuration context.

Applies Rapid Risk Score to focus teams on vulnerabilities most likely to be exploited in the near term.
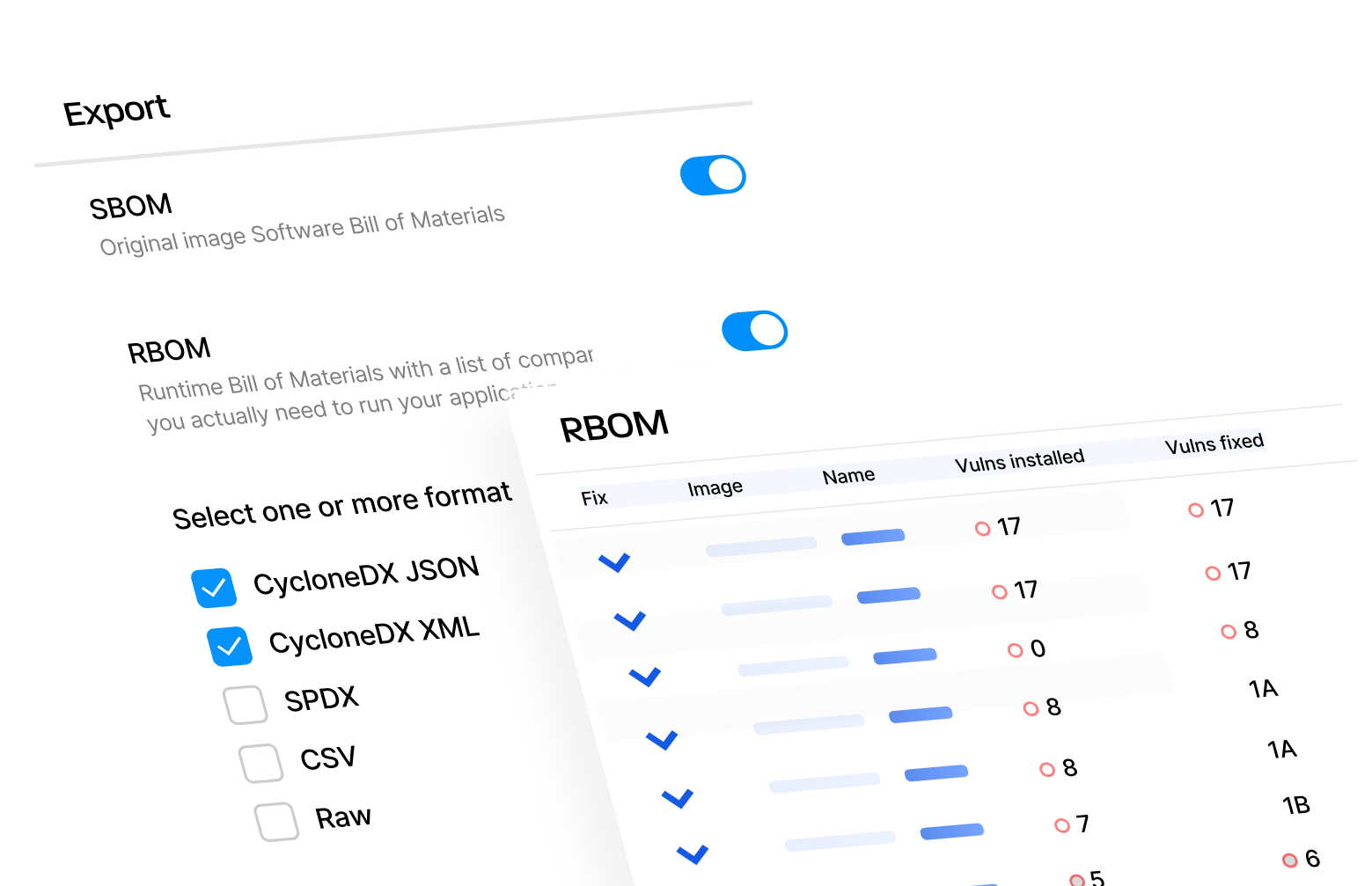
Export SBOMs in SPDX, CycloneDX, JSON, and CSV for audits, compliance, and customer security reviews.

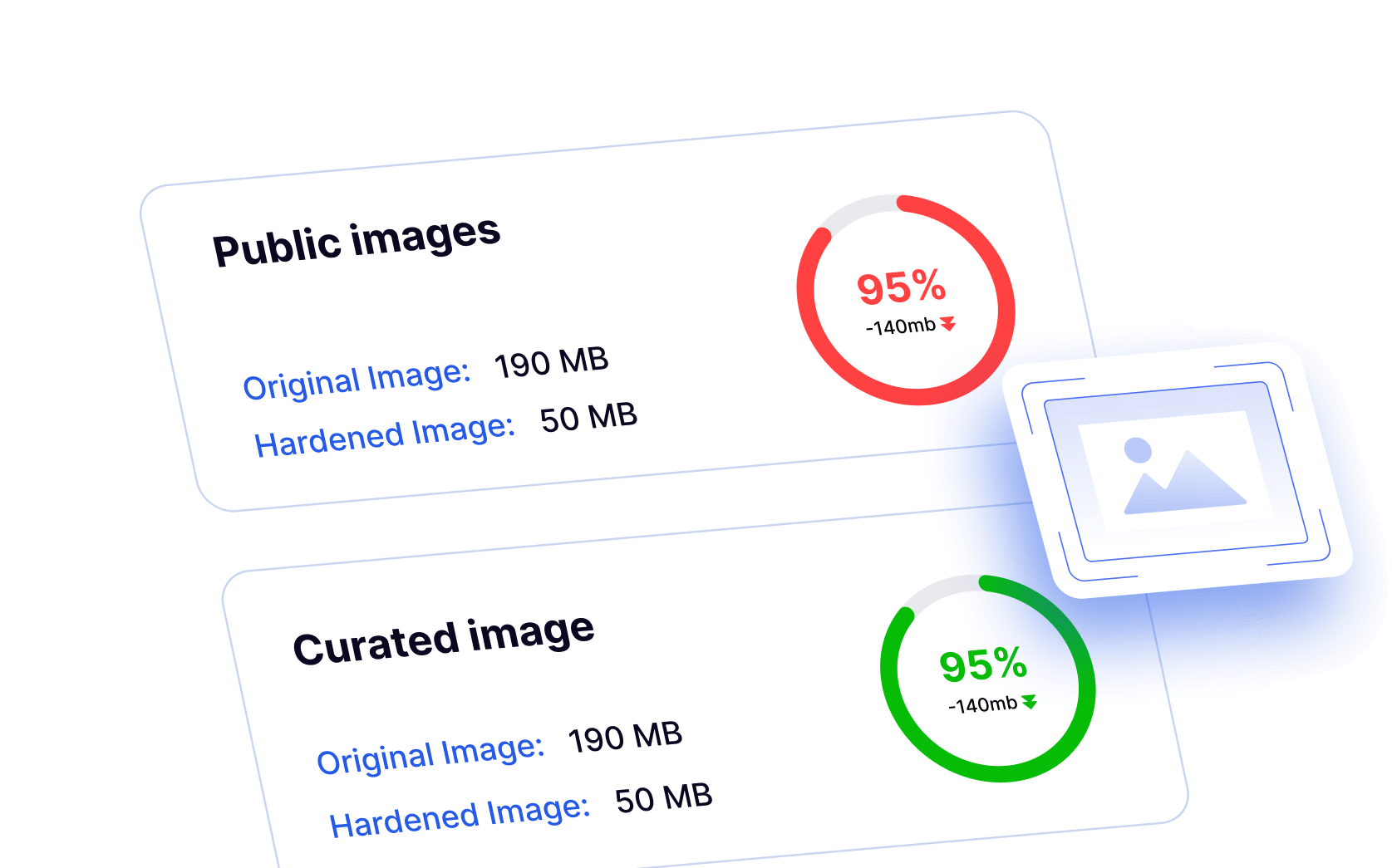
RF Analyzer identifies when vulnerabilities originate from base images and recommends secure, near-zero CVE Curated Images as drop-in replacements.
fewer false positives compared to traditional scanners
and file discovery across container layers
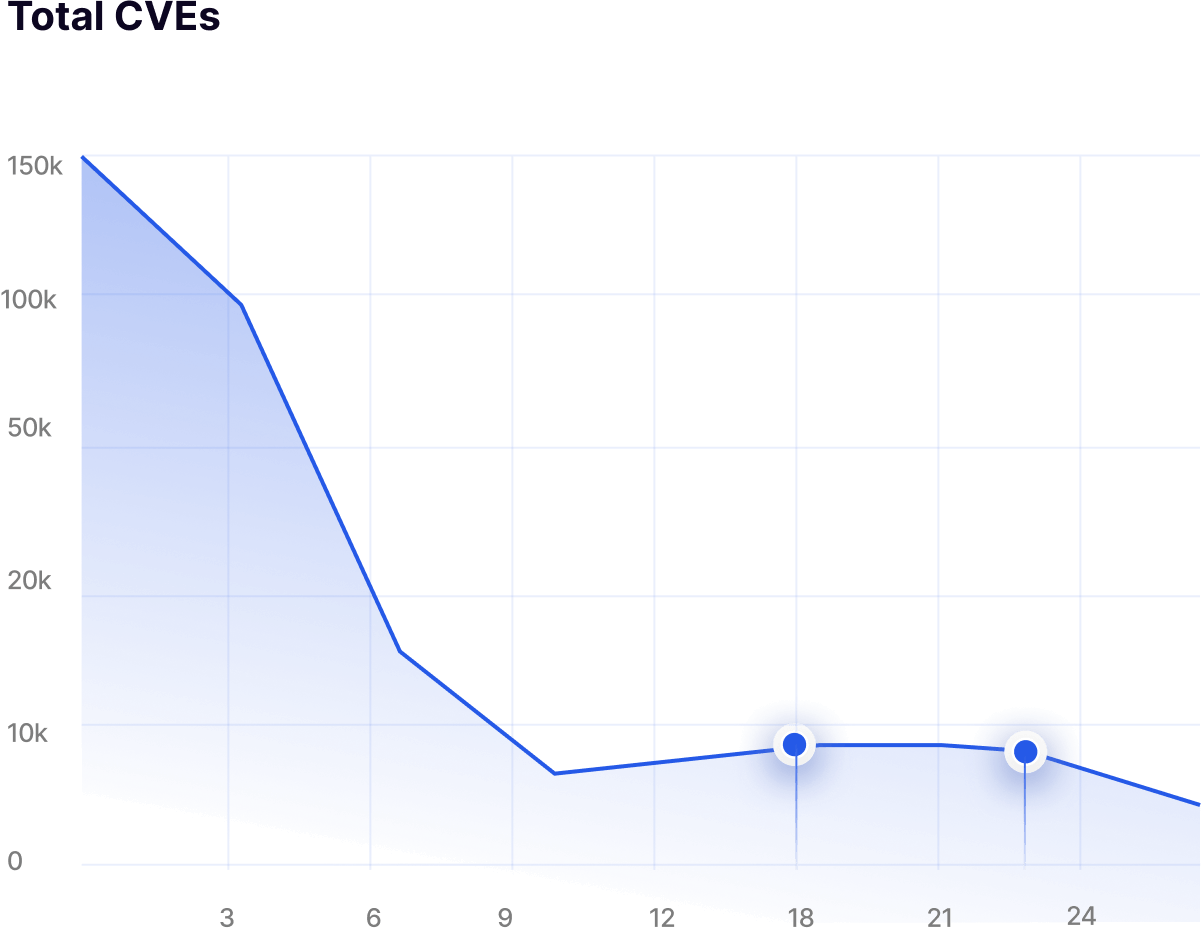
detection of newly published CVEs
footprint optimized for high-speed CI/CD