Security reviews typically focus on the code developers write, but most exposure comes from what ships around it. A large part of every container image is never exercised at runtime - yet it still introduces risk.

Three problem statements:
If a component exists inside the image, it can be scanned, abused, or exploited. Removing risk requires changing what ships, not just what is scanned.
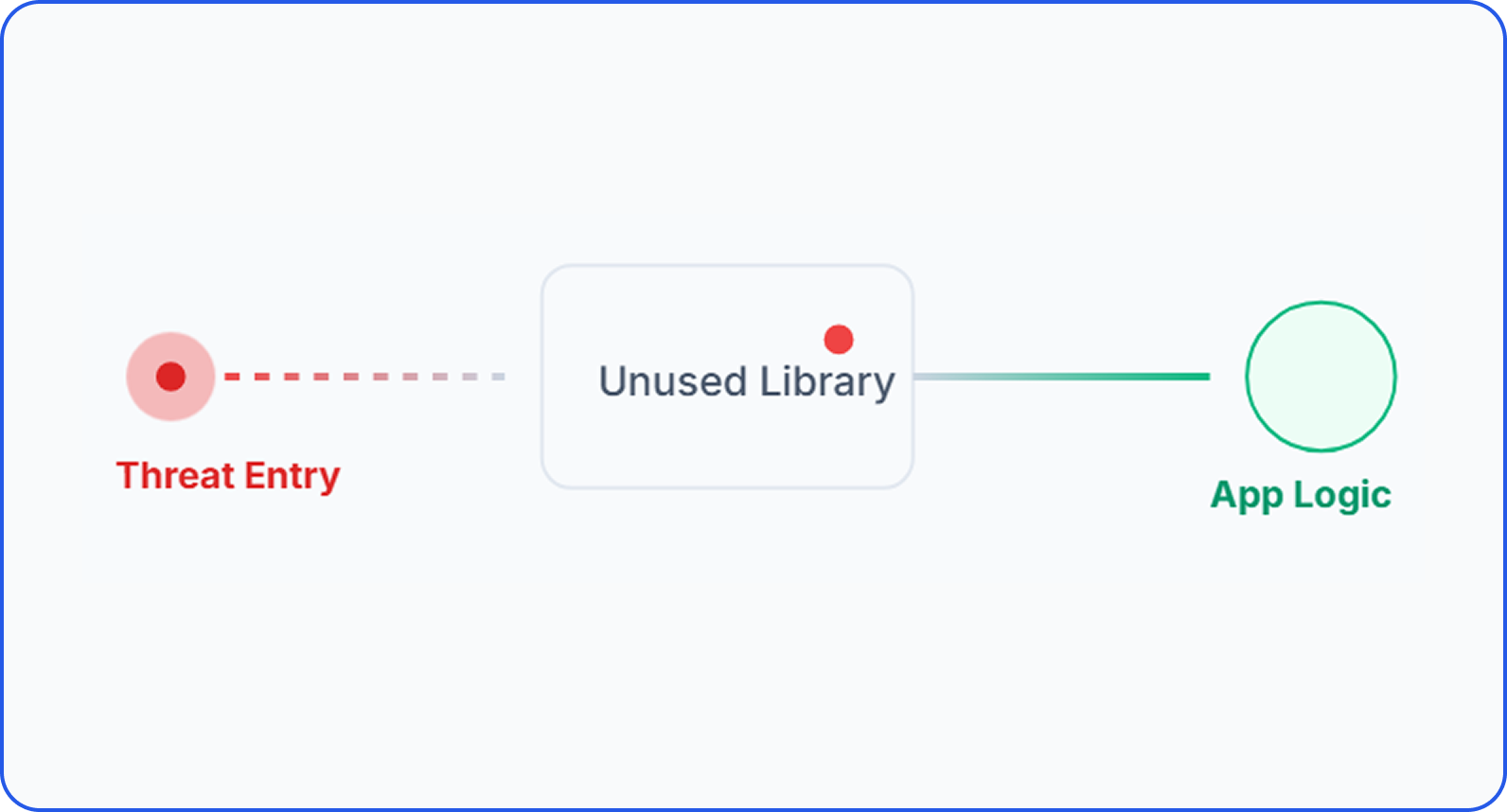
Identify which files, libraries, and binaries actually execute using RBOM visibility.
Start from Curated Near-Zero CVE Images that eliminate inherited OS-level risk.
Remove unused components safely while maintaining application behavior.
reduction in CVEs tied to unused components
Smaller images with faster startup and lower resource usage
Up to 90% reduction in software attack surface
Less manual remediation effort across teams
Achieved on average within 48 hours of deploymen
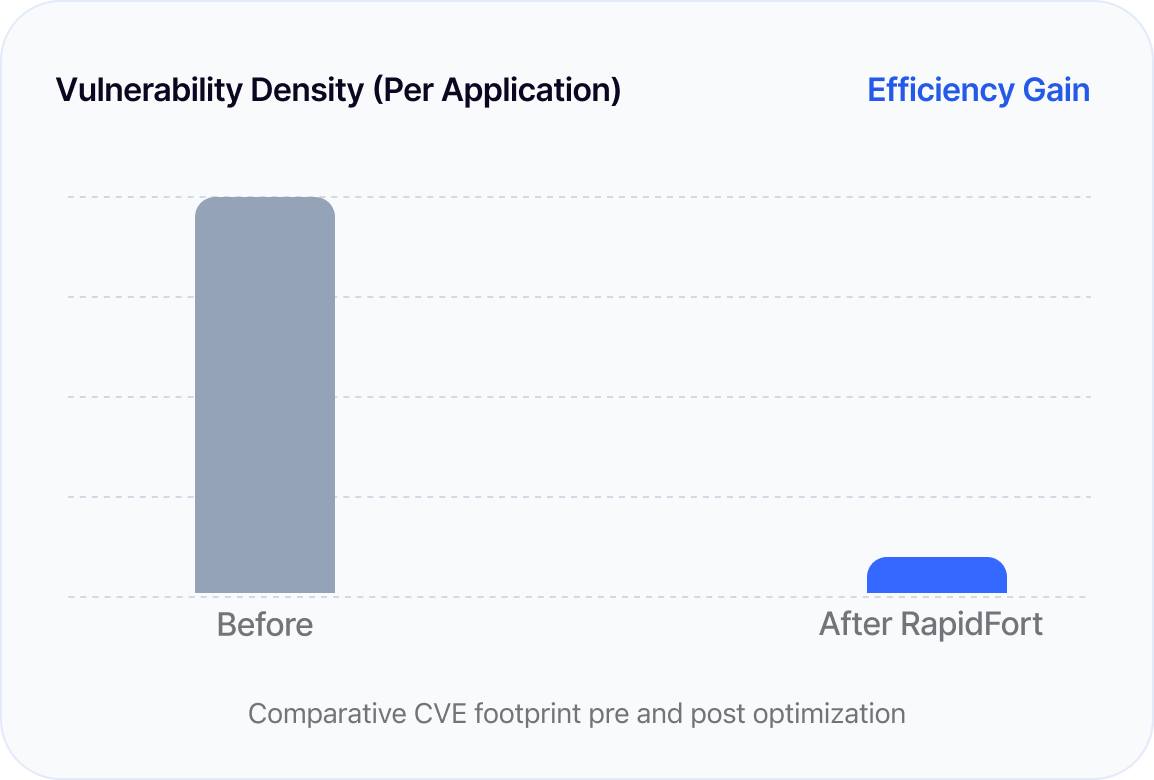
Use runtime-aware optimization to ensure only the code your application actually uses ends up in production.
Security reviews typically focus on the code developers write, but most exposure comes from what ships around it. A large part of every container image is never exercised at runtime - yet it still introduces risk.
RapidFort combines runtime profiling, curated Near-Zero CVE Images, and automated optimization to strip away unused code paths while preserving application behavior.

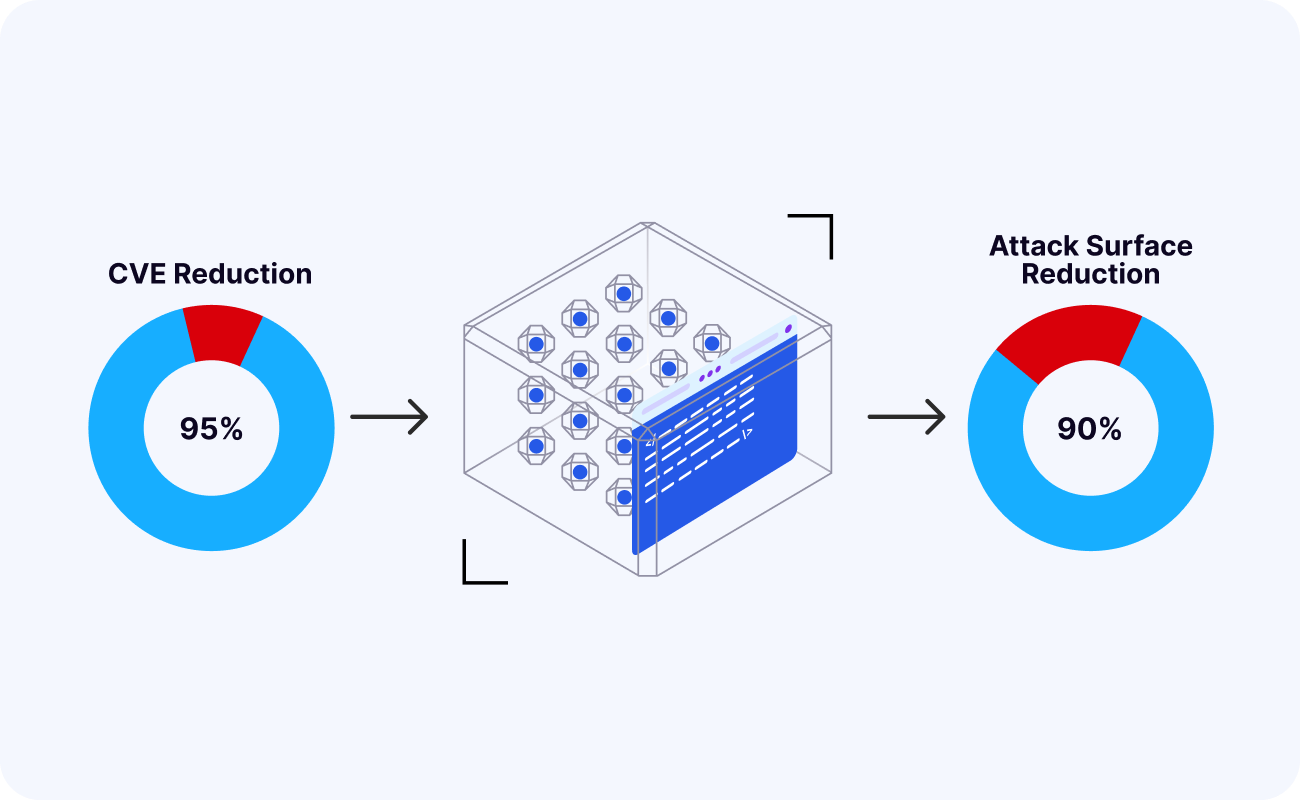

By combining curated foundations, runtime visibility, and automated hardening, RapidFort delivers attack surface reduction that is both visible to security teams and felt by engineering.
Reduction in software attack surface across containerized workloads
Reduction in CVE backlog tied to unused and inherited components
that start faster and consume fewer compute and storage resources
for platform, security, and engineering teams
Attack surface reduction is most effective when it’s built into the software delivery process - not added as another manual step. RapidFort integrates with existing pipelines and environments so each team sees value in their own terms.