Unused libraries and binaries expand reachable vulnerabilities even when untouched by the application.
Patches fix individual CVEs but leave behind bloated OS layers and redundant frameworks.
Teams cannot safely remove unused components at scale without runtime-backed intelligence.
Uses RBOM™ insights to confirm which components are safe to remove - ensuring zero breakage.

Removes entire vulnerable code paths, lowering CVE exposure up to 95%.
Uses RBOM™ insights to confirm which components are safe to remove - ensuring zero breakage.
Lean images improve startup times, reduce cloud costs, and simplify operations.
Achieved by removing unused binaries, libraries, and OS components validated by RBOM execution data.
Delivered by eliminating non-executed code paths from production container images.
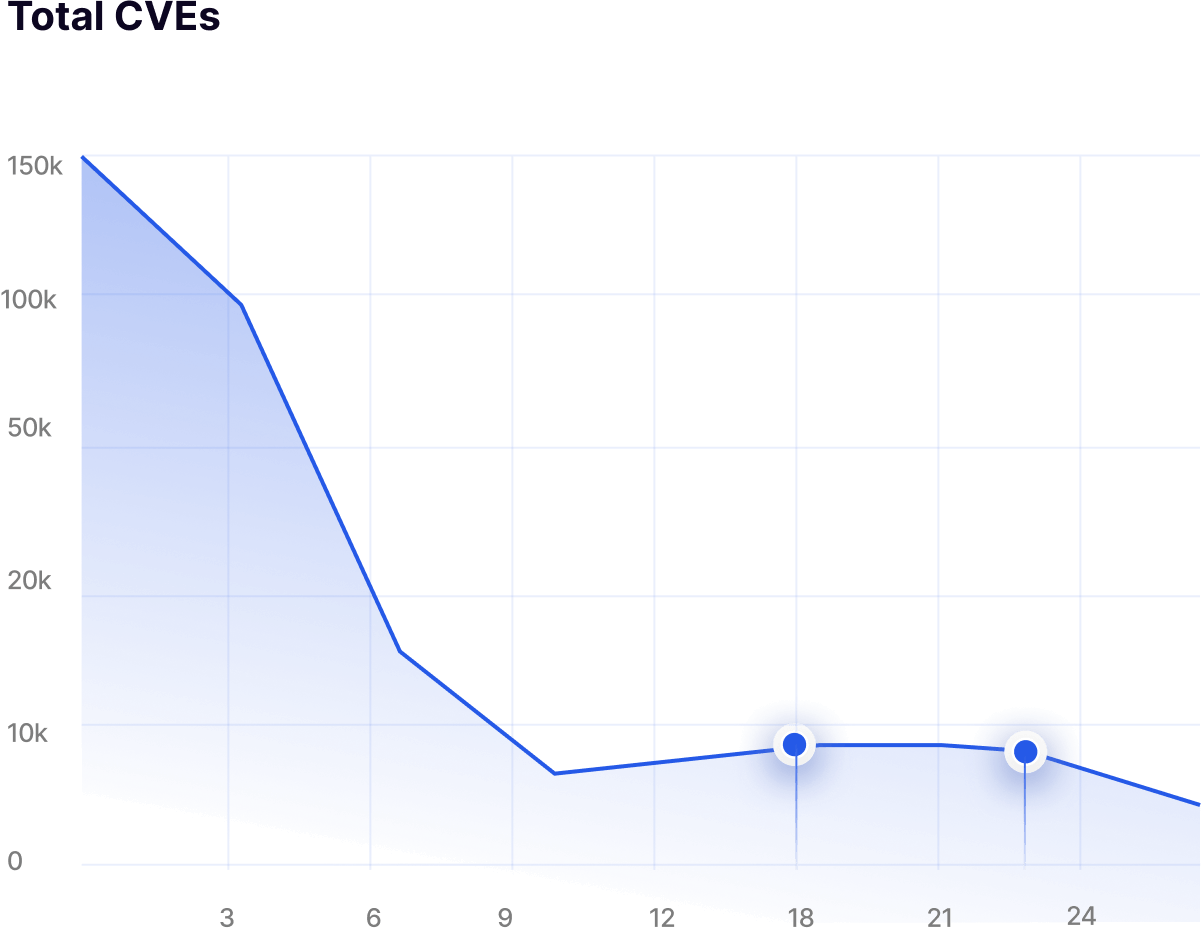
Hardening is execution-aware and does not modify source code, builds, or runtime behavior.
Smaller runtime images improve startup time, resource efficiency, and operational stability.