Reduce inherited risk, validate runtime behavior, and maintain audit-ready evidence continuously.
A continuously updated record of components actually executed in production.
Distinguishes active code paths from dormant layers to reduce noise in vulnerability triage.
Establishes expected runtime behavior and flags deviations that require attention.
Designed for continuous profiling while keeping overhead under 1%.
Identify CVEs in executed components to focus on real, reachable security risks.
Detect unauthorized binaries, configuration changes, or unexpected behavior across clusters.
Provide execution truth needed to safely remove unused components without service disruption.
Achieved by eliminating non-executed packages with vulnerabilities.
Driven by safe removal of unused binaries and libraries.
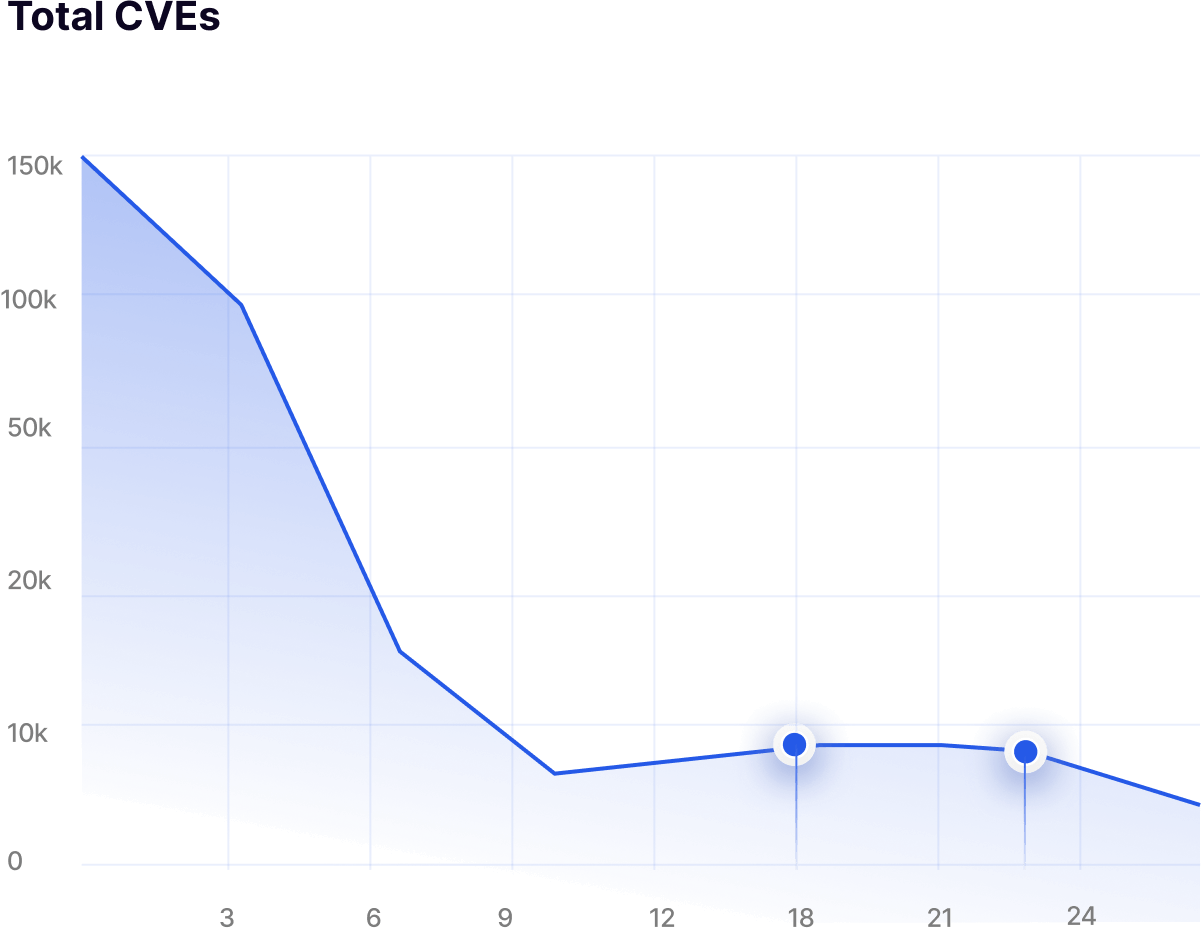
RBOM data shows exactly which package is being used and
Continuous profiling with under 1% overhead and no workload disruption.