Cloud-native delivery, Kubernetes, and frequent releases have outgrown compliance processes designed for static servers and yearly audits.
Evidence is fragmented across scanners, registries, and spreadsheets
Approved baselines drift from what actually runs in production
Teams assemble proof late, under audit and renewal pressure
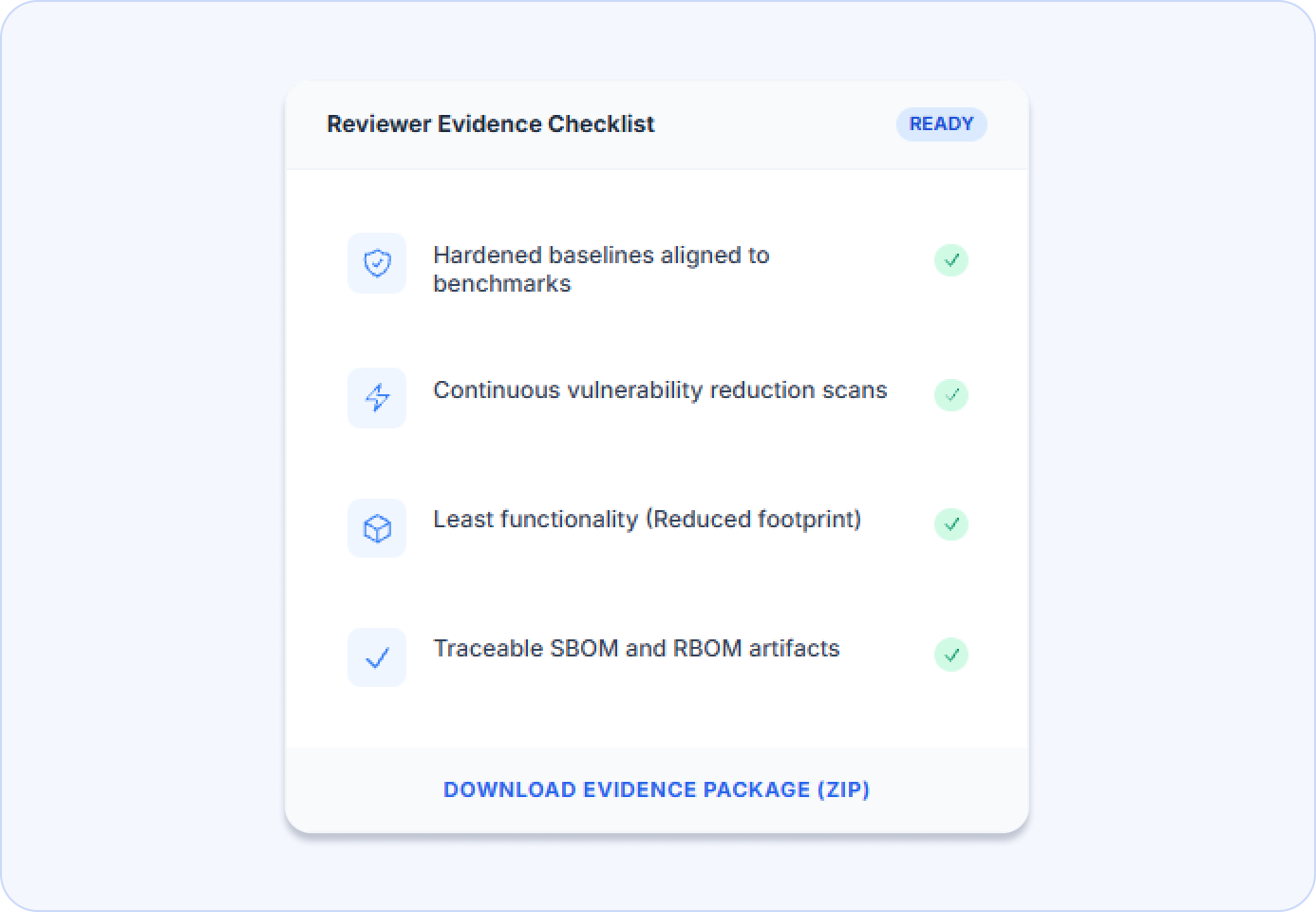
Evidence expectations
Curated Near-Zero CVE Images hardened to CIS and STIG benchmarks and aligned to NIST guidance.
Remove unused components to reduce CVEs and shrink attack surface without changing application logic.
Generate and export SBOM and RBOM artifacts, plus CIS and STIG evidence for audits and reviews.
Achieved through hardened base images and automated attack surface reduction.
SBOM, RBOM, and configuration evidence remain continuously ready for review.
Delivered by removing unused binaries and dormant runtime components.
Automation replaces repetitive vulnerability triage, exception handling, and patch cycles.
Achieved on average within 48 hours of deploymen
Standardize on hardened foundations and maintain continuously ready evidence for regulated reviews and customer assurance.
Cloud-native delivery, Kubernetes, and frequent releases have outgrown compliance processes designed for static servers and yearly audits.
Across FedRAMP, CMMC, HIPAA, PCI DSS, SOC 2, and ISO 27001, the themes are consistent: hardened baselines, continuous vulnerability management, least functionality, and verifiable evidence from build through runtime. RapidFort helps operationalize these requirements for containerized software.
RapidFort connects hardened images, vulnerability reduction, least-functionality enforcement, and runtime verification into a single, explainable story - from what you build to what actually runs.
Outcome
Every audit starts from a defensible, standardized baseline - not a patchwork of public and vendor images.
Outcome
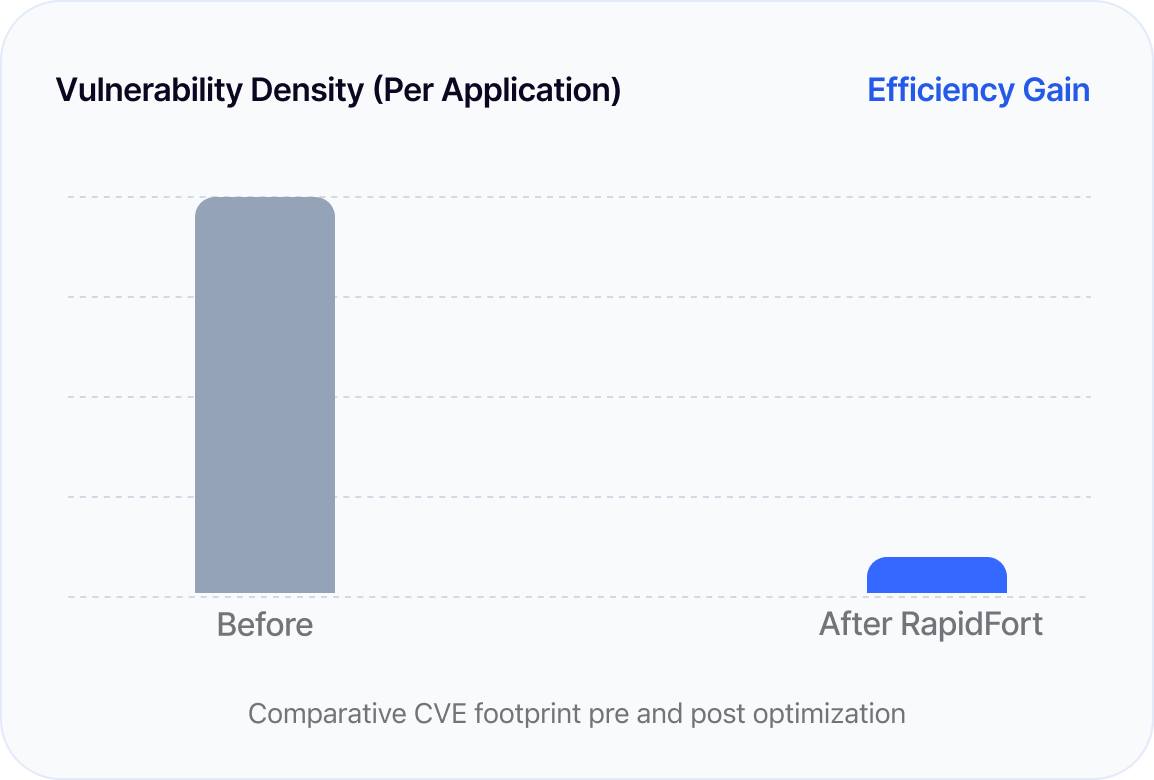
Up to 95% CVE reduction and up to 90% attack-surface reduction, focused on real, runtime-relevant risk.
Outcome
Continuous, control-mapped evidence that can be attached directly to authorization packages, audits, and internal reviews.
Across base images and application containers before code changes are requested.
Through automated removal of unused components and OS layers.
Less time spent on remediation and evidence prep; teams focus on exploitable, runtime-relevant risk.
Faster
Control-mapped SBOM/RBOM™ and CIS/STIG outputs reduce friction with assessors, auditors, and authorizing officials.
Vendors serving federal, healthcare, financial, and critical infrastructure customers can standardize on curated images and attack-surface reduction, demonstrate year-over-year CVE improvement, and attach SBOM/RBOM™ and benchmark reports directly to customer security reviews.
Teams running shared clusters across EKS, AKS, GKE, OpenShift, and on-prem environments gain consistent hardened baselines, runtime RBOM™ visibility, and exportable CIS/STIG and vulnerability evidence for internal and external audits.
CISOs, compliance officers, and GRC owners gain a single, explainable narrative: near-zero CVE baselines, continuous vulnerability management, least functionality by design, and runtime-backed evidence mapped to FedRAMP, CMMC, HIPAA, PCI DSS, SOC 2, and ISO 27001.