Static scans predict intent; runtime reveals truth - and attackers exploit the gap.
Images and scans show what is packaged, not what executes
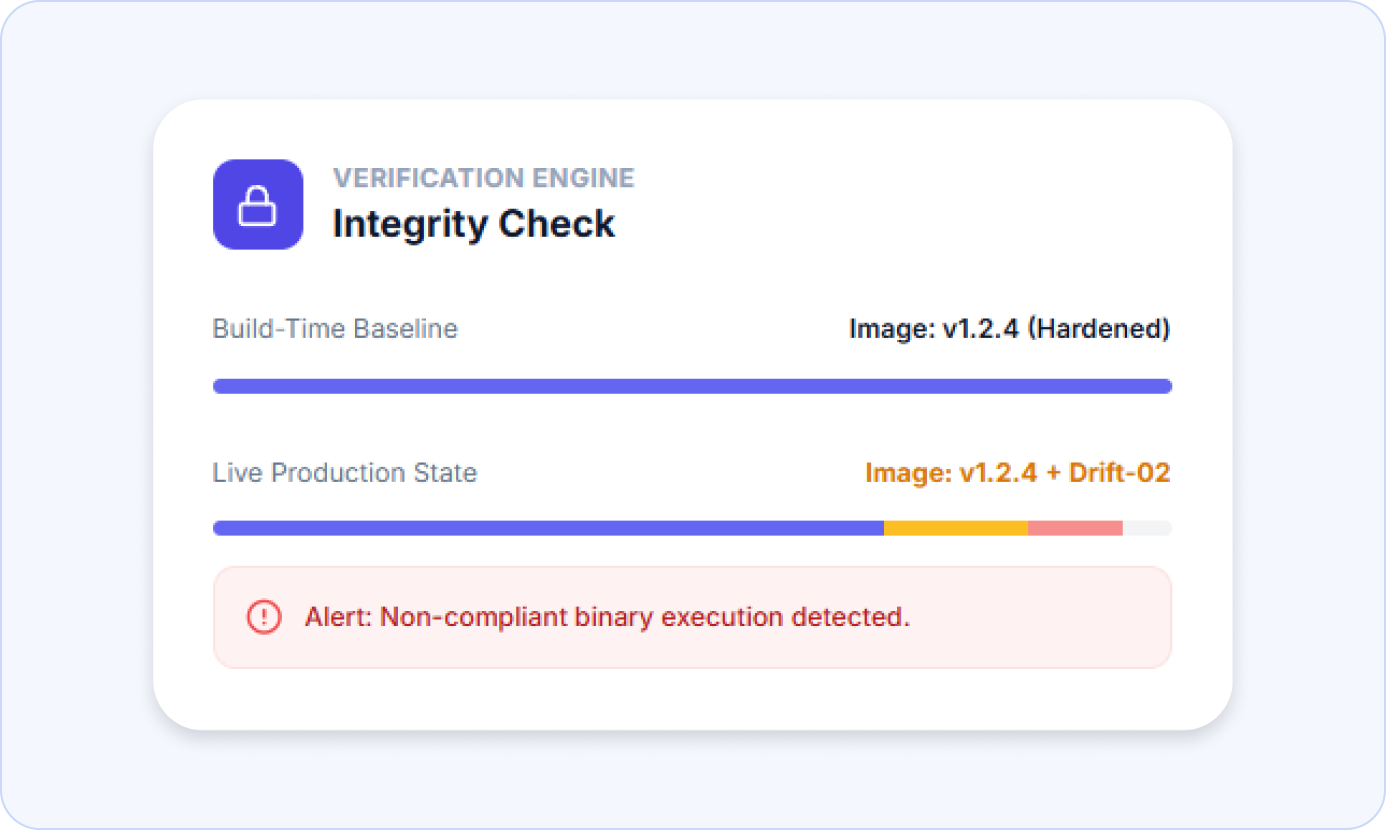
Changes after deployment due to drift and configuration variance
Security teams lack evidence that production matches approved builds
Evidence expectations
RBOM artifacts tied to live workloads
Detection of drift from approved images and configurations
Clear confirmation of which components are actually active in production
Maintain a near-zero CVE posture beyond build time
Reduce uncertainty during incidents and security reviews
Provide continuous, runtime-verified evidence for audits and compliance

Runtime protection ensures that the security posture you approve is the posture that actually exists in production. RapidFort extends vulnerability reduction and hardened foundations into runtime with verifiable evidence.
Static scans predict intent; runtime reveals truth - and attackers exploit the gap.
Containers load binaries and libraries never visible in SBOMs or manifests.
Missed rebuilds, hot patches, and silent config changes distort approved baselines.
Regulated and latency-sensitive clusters cannot run agents - yet still require runtime intelligence.
Static analysis shows what’s inside an image - not what actually runs inside a pod.
Runtime divergence, shadow updates, and unexpected binaries remain invisible without continuous profiling.
Teams struggle to locate where a KEV-vulnerable component is actively loaded.
EKS, AKS, GKE, OpenShift, k3s, and air-gapped clusters behave differently - creating fragmented visibility.
RF Cluster Analyzer surfaces what actually executes inside containers, using only Kubernetes-native, read-only access. No agents. No mutations. No performance hit.
RapidFort connects via Kubernetes APIs only - never modifying workloads.
Runtime profiling reveals:
Outcome
Runtime becomes the most accurate source of truth.
When a risk appears, RapidFort shows:
Outcome
No hunting. No guesswork. No manual correlation.
zero impact on workloads
to identify KEV exposure across clusters
in hybrid & regulated environments
with RBOM-verified lineage