The Reality Financial CISOs Are Up Against
High-risk software inherited from third-party, OSS, and vendor sources
Thousands of CVEs enter financial workloads through public and vendor images before verification, spreading across CI/CD and production systems.
Compliance demands continuous, release-tied evidence
PCI DSS 4.0, SOX 404, and FFIEC guidelines expect ongoing validation, lineage, and configuration assurance—not quarterly snapshots.
Fragmented tools slow remediation and increase audit exposure
Scanner noise, inconsistent SBOMs, and limited drift detection hinder POA&M closure and delay regulatory reviews.
How RapidFort Reduces Financial Software Risk
Start Secure with Curated Near-Zero CVE Foundations

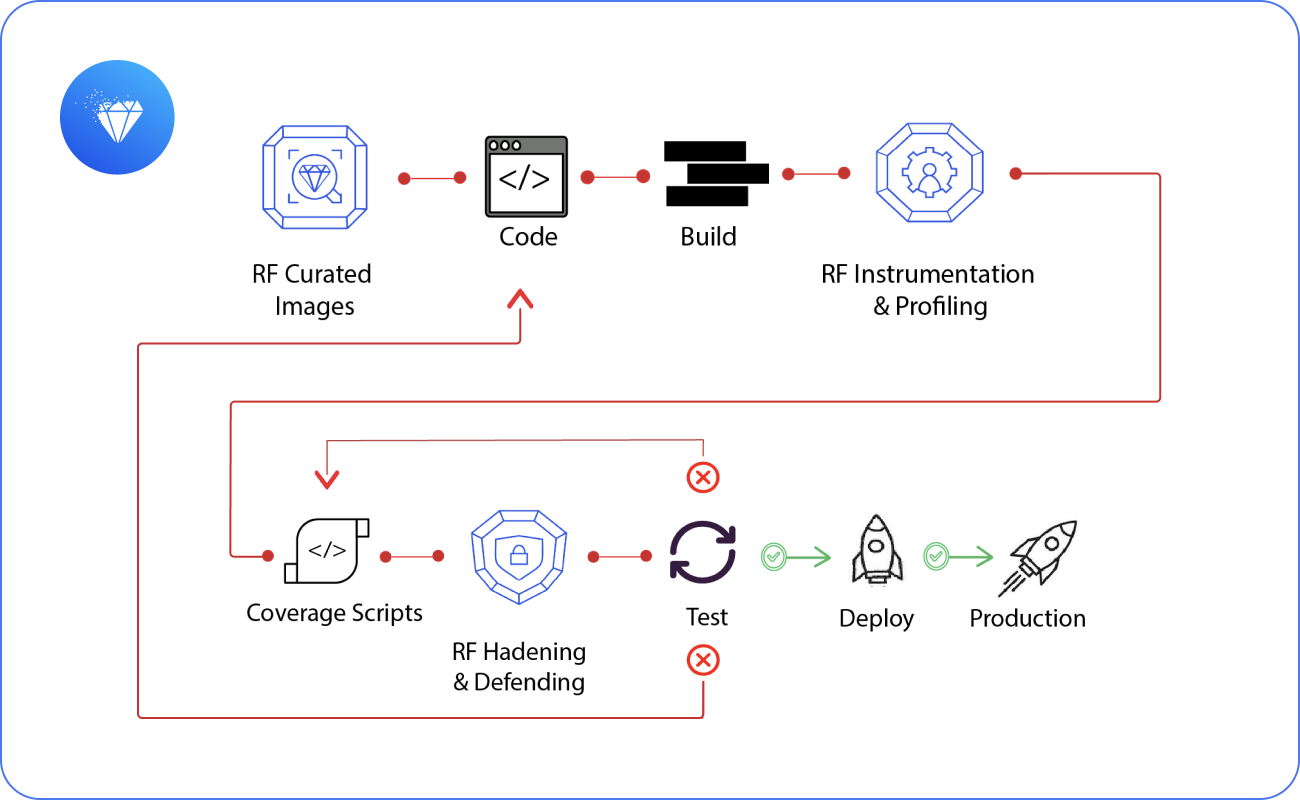
Prioritize True Risk with Analyzer & Profiler Intelligence
Continuously Reduce Exposure with Optimizer & CART
Outcomes Financial Institutions Can Count On
↓ up to 95% CVE reduction
CVE reduction within days
↓ up to 90% attack-surface
Attack-surface reduction across production workloads
~1 week
Audit preparation time reduced from weeks → ~1 week
↓ ~60% Less manual work
Less manual engineering effort through automated workflows
Regulatory Evidence Built Into Every Release

PCI DSS 4.0
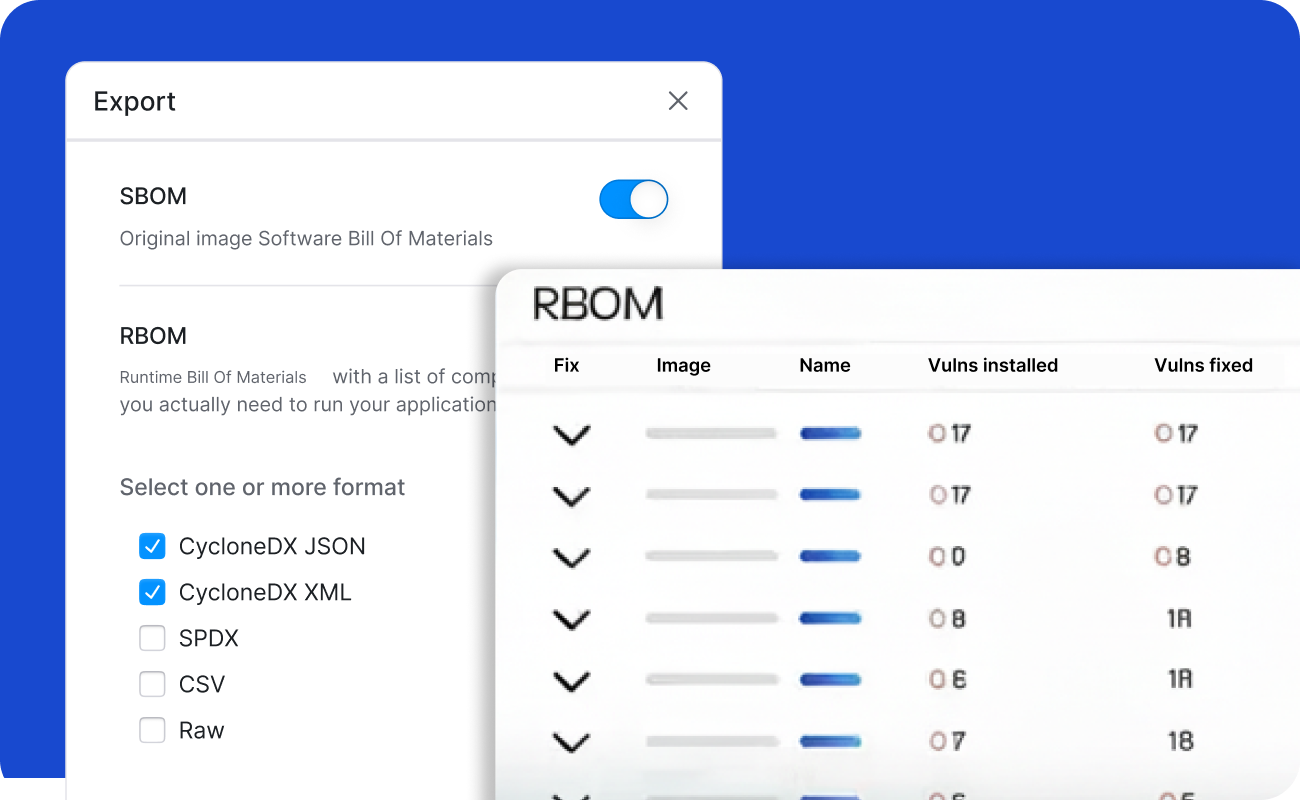
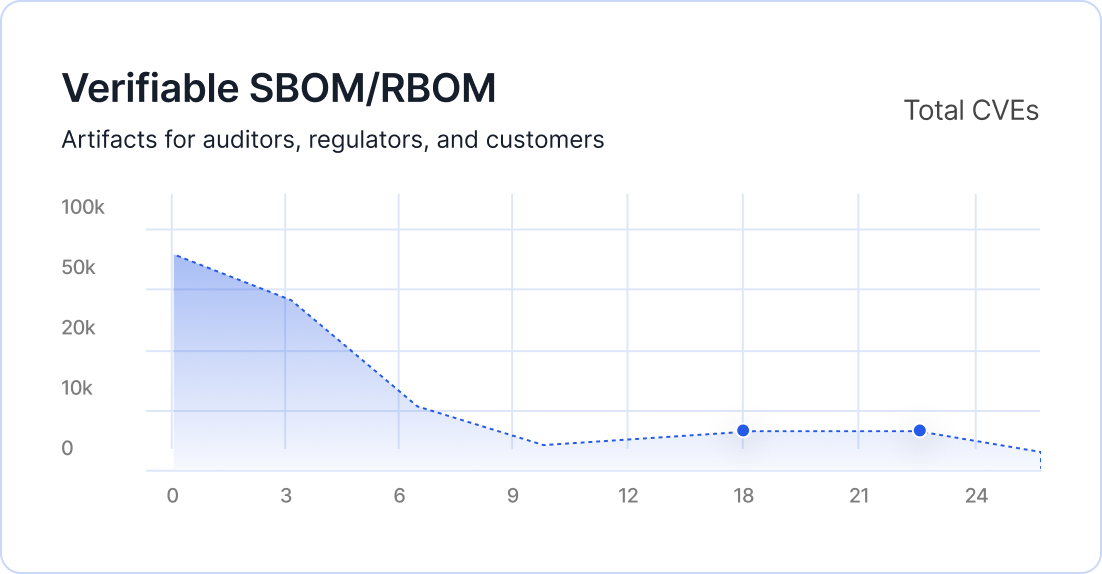
Continuous vulnerability validation and hardened baselines with SBOM/RBOM exports aligned to PCI 4.0 controls.

SOX (Section 404)
Runtime-verified lineage and drift detection supporting defensible change and control testing.

FFIEC & FedRAMP-Relevant Cloud Standards
FIPS-validated, STIG/CIS-aligned container foundations with automated reports for regulated financial cloud environments.

For Internal & External Reviews
Consistent, verifiable artifacts demonstrating continuous risk reduction across the software supply chain.
See what our users think about RapidFort
Frequently asked questions
Answers to Your Most Common Questions
RapidFort is a Software Supply Chain Security platform that helps teams identify, prioritize, and remediate software vulnerabilities—without code changes—by combining DevTime Protection Tools, Curated Near‑Zero CVE Images, and RunTime Protection Tools into a Software Attack Surface Management (SASM) workflow. Typical outcomes include up to 95% CVE remediation and up to 90% attack surface reduction driven by runtime intelligence.
Step 1 — Inventory & Understand (DevTime Protection Tools):
Integrate with your CI/CD pipeline or directly into your Kubernetes environment to scan container images, generate SBOM/RBOM™, reconcile scanner findings, detect drift, and profile execution paths using binary scanning. Outputs include SPDX/CycloneDX reports and RapidRisk Score to prioritize real risk.
Step 2 — Remediate & Automate (Curated Near‑Zero CVE Images):
Drop‑in 10,000+ curated images built on LTS distributions (Alpine, Debian, Red Hat, Ubuntu), hardened with STIG/CIS in alignment with NIST SP 800‑70, with FIPS 140‑3 validation and continuous patching—so teams start with near zero CVEs. No vendor lock‑in.
Step 3 — Maintain & Defend (RunTime Protection Tools):
Enforces runtime‑guided hardening to remove unused components, continuously monitors baselines, and alerts on anomalies—achieving up to 95% CVE remediation and up to 90% attack surface reduction with <1% compute overhead.
They are production‑grade base images that are continuously patched and scanned, available across LTS Linux (Alpine, Debian, Red Hat, Ubuntu), hardened using STIG/CIS benchmarks (aligned to NIST SP 800‑70), and offered at scale (10,000+ images). They are designed to accelerate FedRAMP/CMMC/SOC 2 readiness and avoid lock‑in by using widely adopted distributions.
Secure Your Financial Software Supply Chain Today
Reduce systemic risk, accelerate compliance readiness, and safeguard every transaction with continuous, end-to-end security across your software supply chain.