The Security Realities Driving Healthcare Risk
Inherited vulnerabilities across third-party, vendor, and OSS components
EHR platforms, medical devices, imaging systems, and analytics pipelines carry significant CVE debt before verification—putting PHI and operational systems at risk.
HIPAA, HITRUST & FDA demand continuous cybersecurity validation
Regulators expect ongoing vulnerability identification, mitigation evidence, and component lineage—not periodic manual assessments.
Clinical uptime constraints limit patching and code changes
Traditional remediation methods risk device recertification, workflow disruption, and service downtime—making non-invasive security essential.
How RapidFort Reduces Healthcare Software Risk
Start Secure with Curated Near-Zero CVE Foundations

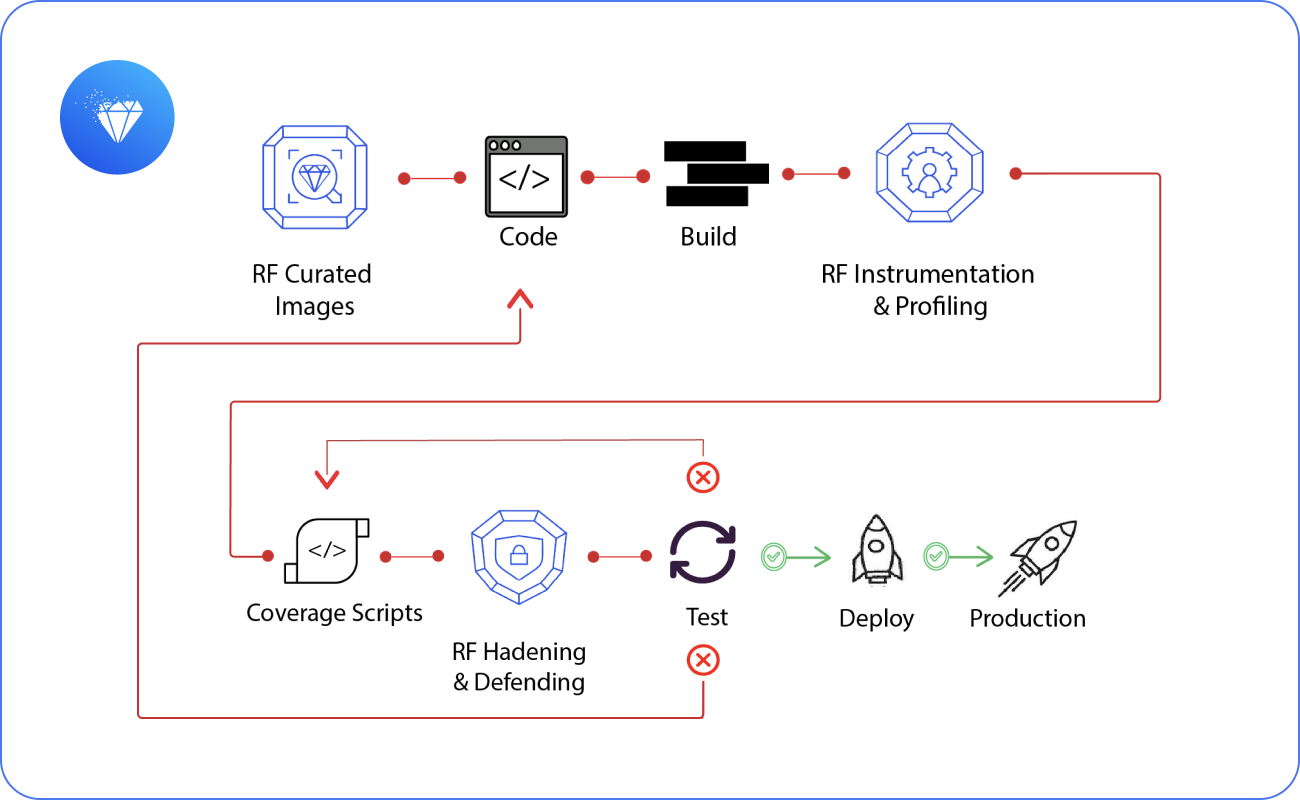
Prioritize True Risk with Analyzer & Profiler Intelligence
Continuously Reduce Exposure with Optimizer & CART
Outcomes Healthcare Organizations Can Count On
↓ up to 95% CVE reduction
CVE reduction across healthcare and MedTech workloads
↓ up to 90% attack-surface
Attack-surface reduction via zero-code hardening
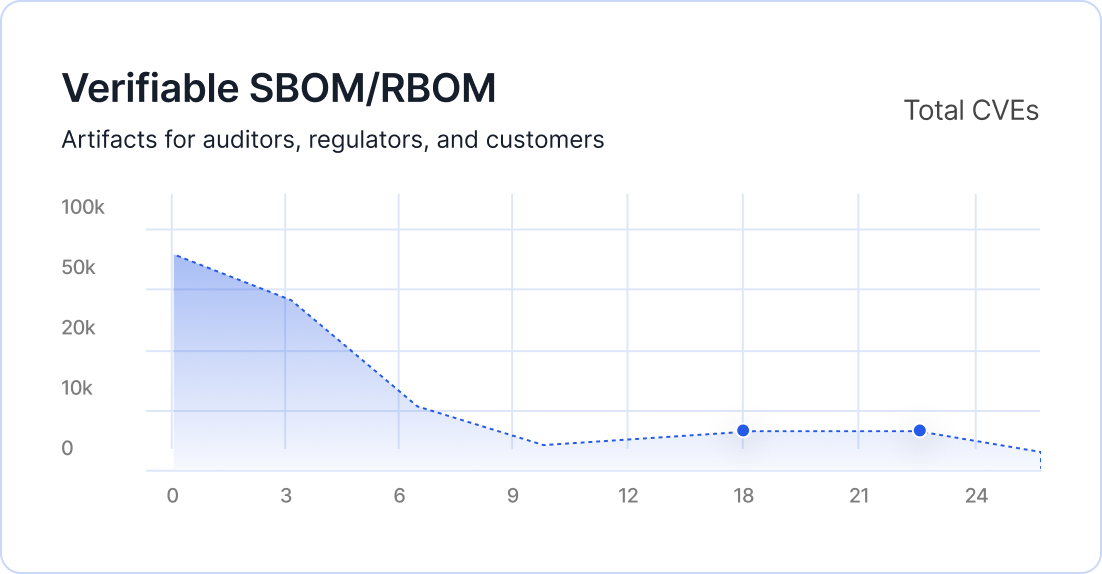
Weeks → Days
Days instead of weeks to generate audit-ready evidence
↓ ~60% Less manual work
Less manual security and patching effort
Compliance-Ready Evidence for Healthcare Regulators

HIPAA / HITRUST CSF
Continuous vulnerability validation and SBOM/RBOM outputs aligned to HIPAA safeguards and HITRUST control requirements.

FDA 21 CFR Cybersecurity Readiness
Verified SBOMs, exploitable-risk analysis, and mitigation traceability supporting premarket and postmarket cybersecurity expectations.

SOC 2 / ISO 27001 Alignment
Automated CIS/STIG checks and configuration evidence mapped to SOC 2 trust principles and ISO Annex A controls.

Healthcare Vendor & Partner Assurance
Consistent, verifiable evidence accelerating BAAs, procurement reviews, and third-party security assessments.
See what our users think about RapidFort
Frequently asked questions
Answers to Your Most Common Questions
RapidFort is a Software Supply Chain Security platform that helps teams identify, prioritize, and remediate software vulnerabilities—without code changes—by combining DevTime Protection Tools, Curated Near‑Zero CVE Images, and RunTime Protection Tools into a Software Attack Surface Management (SASM) workflow. Typical outcomes include up to 95% CVE remediation and up to 90% attack surface reduction driven by runtime intelligence.
Step 1 — Inventory & Understand (DevTime Protection Tools):
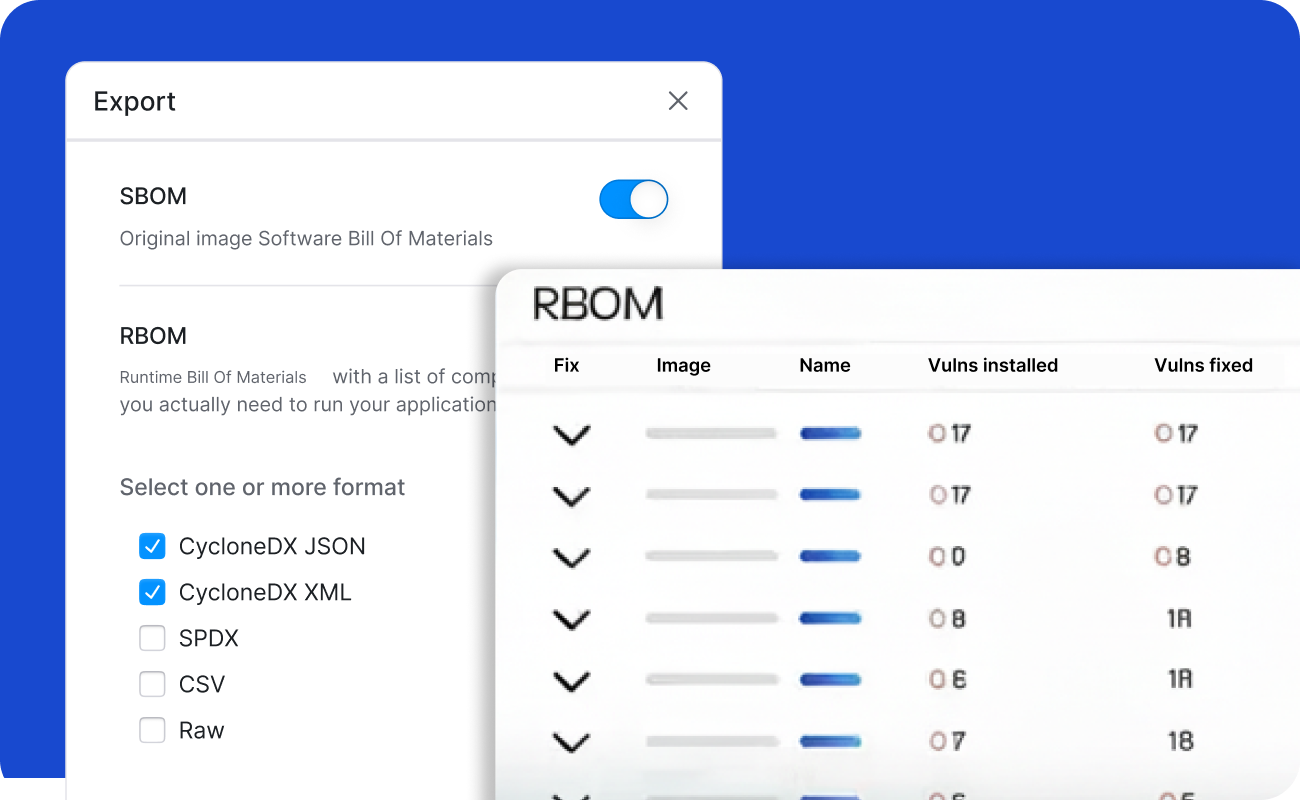
Integrate with your CI/CD pipeline or directly into your Kubernetes environment to scan container images, generate SBOM/RBOM™, reconcile scanner findings, detect drift, and profile execution paths using binary scanning. Outputs include SPDX/CycloneDX reports and RapidRisk Score to prioritize real risk.
Step 2 — Remediate & Automate (Curated Near‑Zero CVE Images):
Drop‑in 10,000+ curated images built on LTS distributions (Alpine, Debian, Red Hat, Ubuntu), hardened with STIG/CIS in alignment with NIST SP 800‑70, with FIPS 140‑3 validation and continuous patching—so teams start with near zero CVEs. No vendor lock‑in.
Step 3 — Maintain & Defend (RunTime Protection Tools):
Enforces runtime‑guided hardening to remove unused components, continuously monitors baselines, and alerts on anomalies—achieving up to 95% CVE remediation and up to 90% attack surface reduction with <1% compute overhead.
They are production‑grade base images that are continuously patched and scanned, available across LTS Linux (Alpine, Debian, Red Hat, Ubuntu), hardened using STIG/CIS benchmarks (aligned to NIST SP 800‑70), and offered at scale (10,000+ images). They are designed to accelerate FedRAMP/CMMC/SOC 2 readiness and avoid lock‑in by using widely adopted distributions.
Protect Patient Data. Strengthen Compliance. Secure Healthcare at Scale.
Gain the visibility, vulnerability control, and compliance-ready evidence needed to protect patients and accelerate digital health innovation.