The Security Realities Driving Software Risk
Upstream code introduces silent, high-volume vulnerability risk
Software companies depend heavily on OSS packages, public images, and vendor components — and inherit CVE debt automatically as it flows through CI/CD and into production.
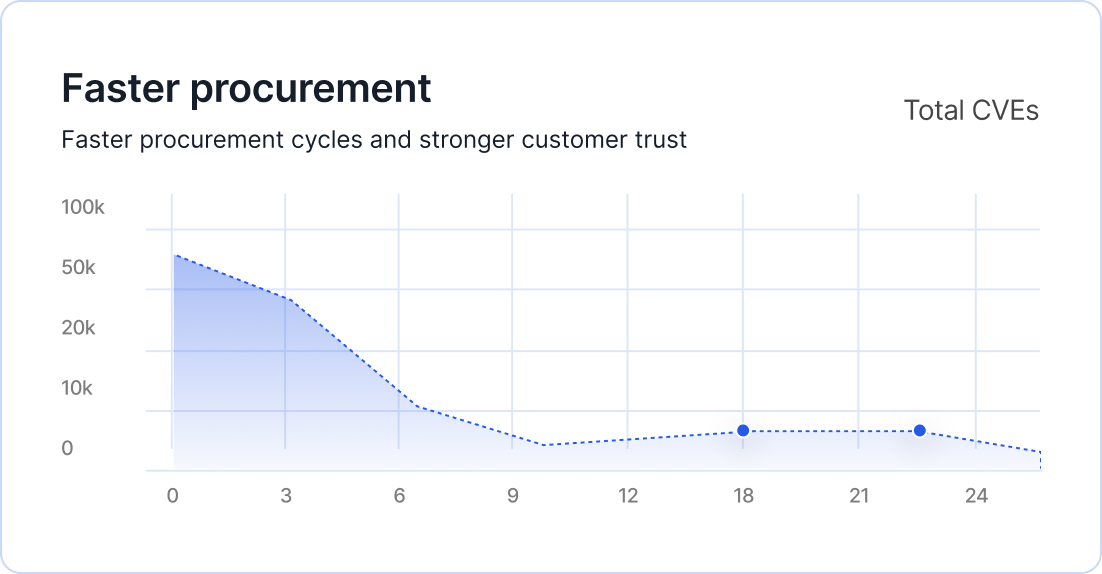
Customer security expectations slow down sales cycles
Enterprise buyers now expect SBOMs, RBOMs, vulnerability exposure details, and continuous evidence. Producing this manually delays procurement, onboarding, and renewals.
Rapid development outpaces traditional patching and scanning
Frequent releases make it impossible to rebuild and revalidate images manually. Without runtime visibility, organizations cannot prove which components actually execute in production.
How RapidFort Reduces Software Supply Chain Risk
Start Secure with Curated Near-Zero CVE Foundations

Prioritize True Risk with Analyzer & Profiler Intelligence
Continuously Reduce Exposure with Optimizer & CART
Outcomes Software Companies Rely On
↓ up to 95% CVE reduction
CVE reduction across microservices, APIs, and backend systems
↓ up to 90% Attack-surface
Attack-surface reduction without slowing releases
Weeks → Days
Enterprise security reviews completed in days, not weeks
↓ ~60% Reduction
reduction in manual remediation effort
Compliance-Ready Evidence for Enterprise Buyers

SOC 2 (Type II)
Continuous vulnerability validation, hardened baselines, and SBOM/RBOM artifacts aligned with SOC 2 trust principles.

ISO 27001 (Annex A)
STIG/CIS-aligned configurations and verifiable evidence supporting Annex A controls for configuration and vulnerability management.

FedRAMP & Public Sector Customers
FIPS-validated, STIG-aligned container baselines and continuous remediation outputs supporting FedRAMP-aligned readiness.

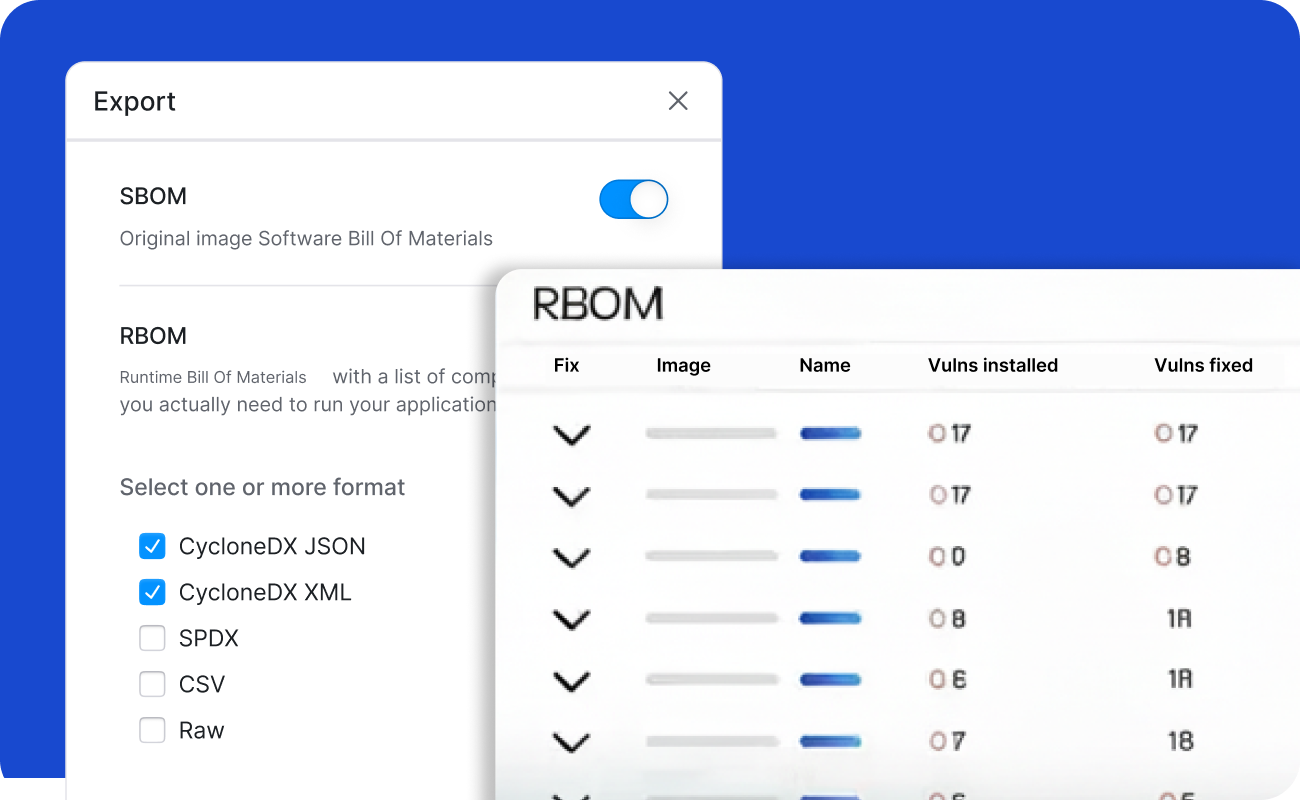
Customer Due Diligence & Security Reviews
On-demand SBOM/RBOM exports, KEV exposure details, and vulnerability evidence packages for procurement teams.
See what our users think about RapidFort
Frequently asked questions
Answers to Your Most Common Questions
RapidFort is a Software Supply Chain Security platform that helps teams identify, prioritize, and remediate software vulnerabilities—without code changes—by combining DevTime Protection Tools, Curated Near‑Zero CVE Images, and RunTime Protection Tools into a Software Attack Surface Management (SASM) workflow. Typical outcomes include up to 95% CVE remediation and up to 90% attack surface reduction driven by runtime intelligence.
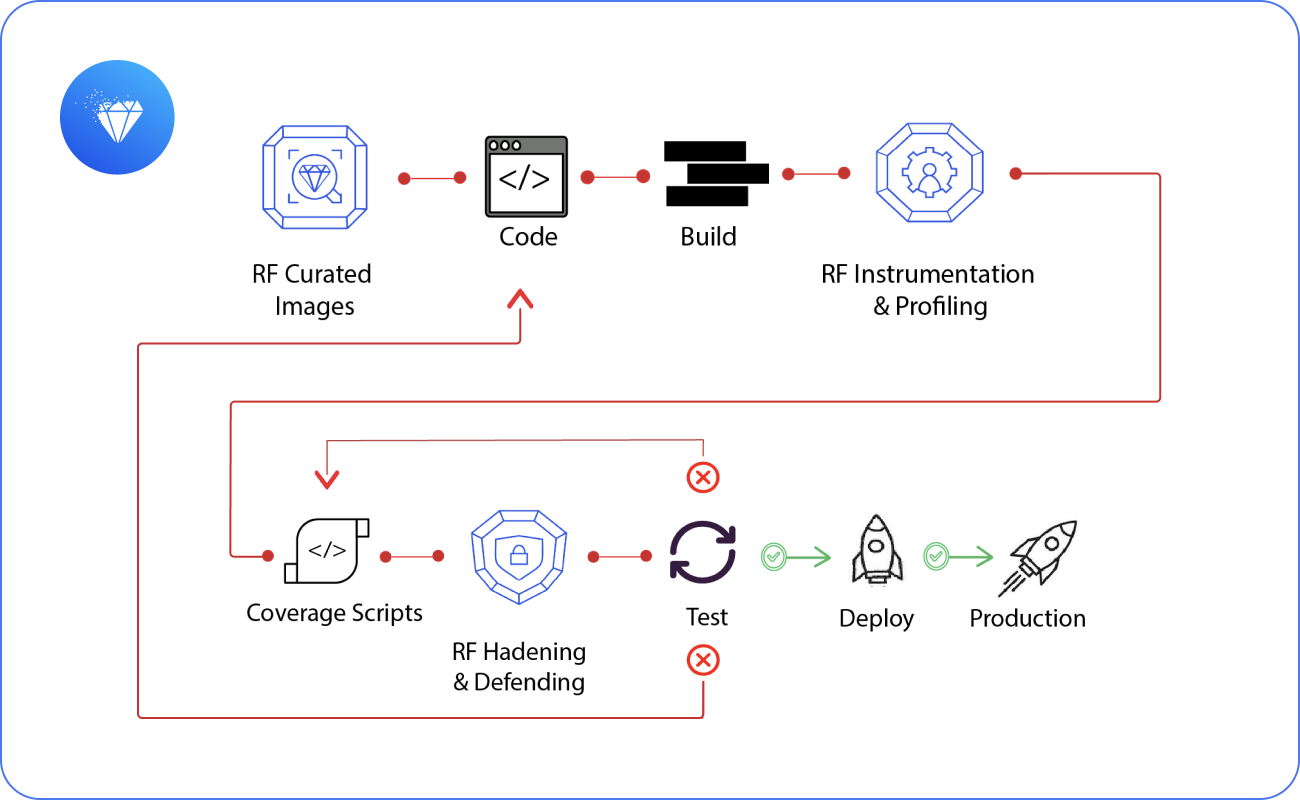
Step 1 — Inventory & Understand (DevTime Protection Tools):
Integrate with your CI/CD pipeline or directly into your Kubernetes environment to scan container images, generate SBOM/RBOM™, reconcile scanner findings, detect drift, and profile execution paths using binary scanning. Outputs include SPDX/CycloneDX reports and RapidRisk Score to prioritize real risk.
Step 2 — Remediate & Automate (Curated Near‑Zero CVE Images):
Drop‑in 10,000+ curated images built on LTS distributions (Alpine, Debian, Red Hat, Ubuntu), hardened with STIG/CIS in alignment with NIST SP 800‑70, with FIPS 140‑3 validation and continuous patching—so teams start with near zero CVEs. No vendor lock‑in.
Step 3 — Maintain & Defend (RunTime Protection Tools):
Enforces runtime‑guided hardening to remove unused components, continuously monitors baselines, and alerts on anomalies—achieving up to 95% CVE remediation and up to 90% attack surface reduction with <1% compute overhead.
They are production‑grade base images that are continuously patched and scanned, available across LTS Linux (Alpine, Debian, Red Hat, Ubuntu), hardened using STIG/CIS benchmarks (aligned to NIST SP 800‑70), and offered at scale (10,000+ images). They are designed to accelerate FedRAMP/CMMC/SOC 2 readiness and avoid lock‑in by using widely adopted distributions.
Secure Your Software Supply Chain — End to End.
Harden what you build. Prove what you ship. Strengthen every customer deployment with runtime-verified, continuously remediated software.