The Security Realities Driving Mission Software Risk
Inherited risk slows ATO and expands POA&Ms
Vendor and open-source images often arrive with large CVE backlogs, delaying ATO decisions, complicating FedRAMP packages, and inflating POA&M lists.
Continuous authorization demands continuous evidence
cATO, ConMon, and zero-trust directives require ongoing vulnerability reduction and traceable lineage tied to each release—not quarterly scans or static screenshots.
Fragmented visibility across diverse environments
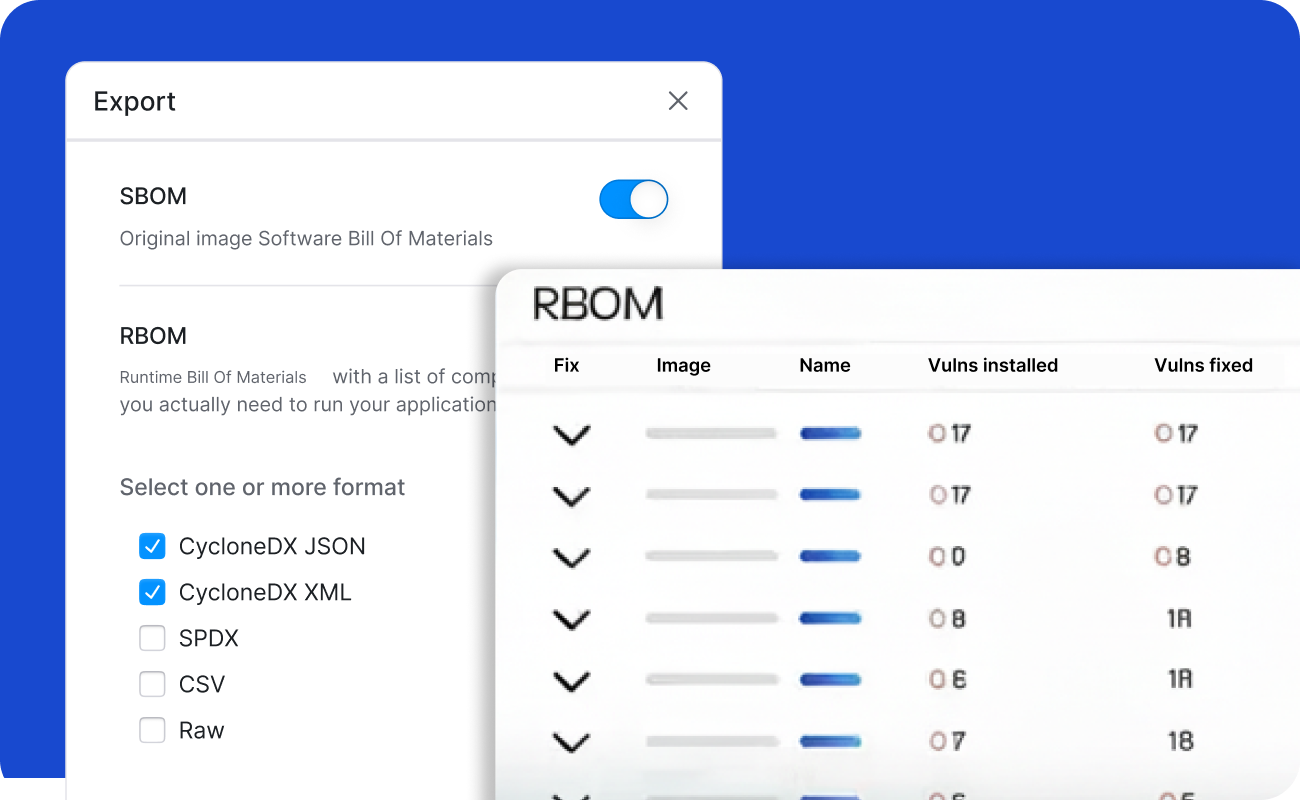
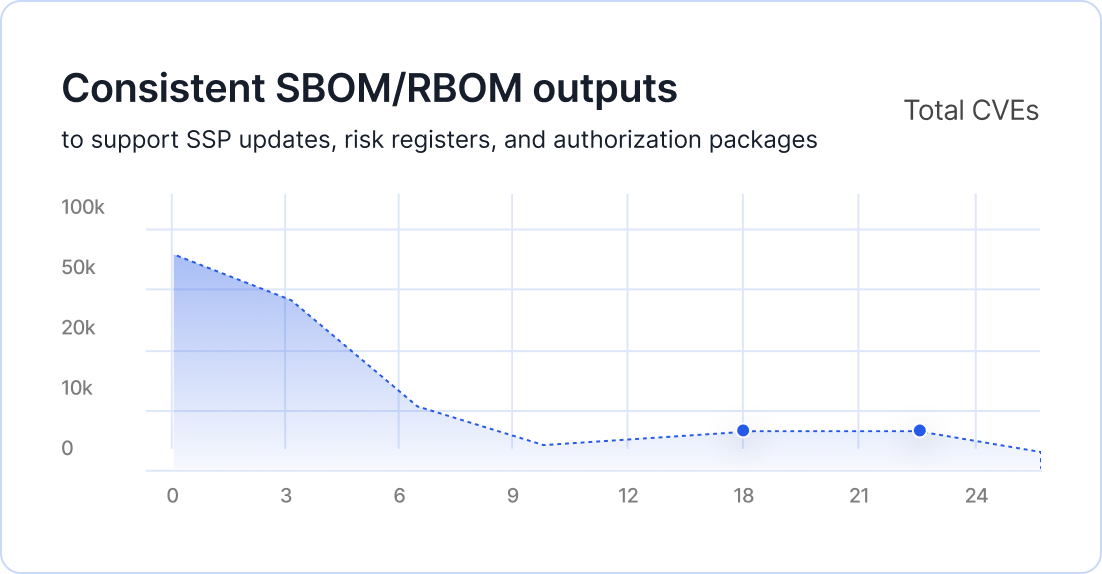
Programs span multiple clouds, on-prem, and restricted networks. Without clear runtime visibility and consistent SBOM/RBOM outputs, it is difficult to reconcile CVE counts, track drift, or validate that approved baselines match what is actually running.
How RapidFort Reduces Mission Software Risk
Start on Hardened, Near-Zero CVE Baselines

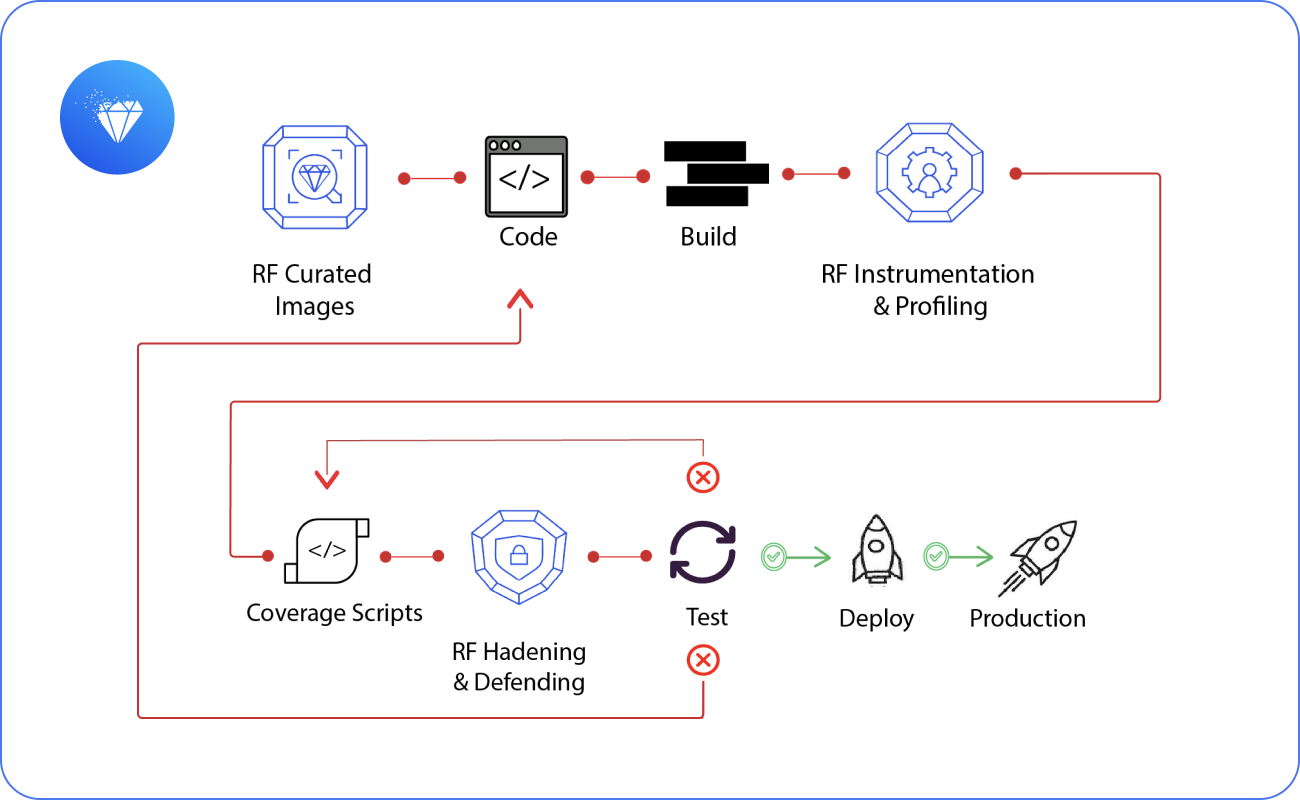
Expose and Prioritize True Risk with Analyzer & Profiler
Continuously Reduce Exposure with Optimizer & CART
Outcomes Mission Programs Can Rely On
↓ up to 95% reduction
in CVEs across containerized mission workloads
↓ up to 90% reduction
in software attack surface through automated hardening
Months → Continuous
faster production of security evidence for cATO, ConMon, and POA&M updates
↓ ~60% Less manual work
by replacing rebuilds with automated, zero-code remediation
Audit-Aligned Evidence for Authorization Officials

CMMC 2.0 / NIST 800-171
Continuous vulnerability identification and reduction backed by hardened baselines and SBOM/RBOM outputs. Artifacts that support control families related to risk assessment, configuration management, and vulnerability management.

FedRAMP (NIST 800-53 Rev. 5) & StateRAMP
STIG/CIS-aligned containers and continuous remediation data that feed into FedRAMP and State RAMP ConMon processes. Exportable SBOM/RBOM to support SSPs, security assessments, and POA&M tracking.

FISMA-Aligned Federal Systems
Hardened baselines and vulnerability-reduction metrics that map to NIST 800-53 control expectations for federal information systems.

cATO and Zero-Trust Initiatives
Runtime-verified lineage (RBOM™), drift detection, and continuous CVE reduction to support repeatable risk validation within authorization boundaries.
See what our users think about RapidFort
Frequently asked questions
Answers to Your Most Common Questions
RapidFort is a Software Supply Chain Security platform that helps teams identify, prioritize, and remediate software vulnerabilities—without code changes—by combining DevTime Protection Tools, Curated Near‑Zero CVE Images, and RunTime Protection Tools into a Software Attack Surface Management (SASM) workflow. Typical outcomes include up to 95% CVE remediation and up to 90% attack surface reduction driven by runtime intelligence.
Step 1 — Inventory & Understand (DevTime Protection Tools):
Integrate with your CI/CD pipeline or directly into your Kubernetes environment to scan container images, generate SBOM/RBOM™, reconcile scanner findings, detect drift, and profile execution paths using binary scanning. Outputs include SPDX/CycloneDX reports and RapidRisk Score to prioritize real risk.
Step 2 — Remediate & Automate (Curated Near‑Zero CVE Images):
Drop‑in 10,000+ curated images built on LTS distributions (Alpine, Debian, Red Hat, Ubuntu), hardened with STIG/CIS in alignment with NIST SP 800‑70, with FIPS 140‑3 validation and continuous patching—so teams start with near zero CVEs. No vendor lock‑in.
Step 3 — Maintain & Defend (RunTime Protection Tools):
Enforces runtime‑guided hardening to remove unused components, continuously monitors baselines, and alerts on anomalies—achieving up to 95% CVE remediation and up to 90% attack surface reduction with <1% compute overhead.
They are production‑grade base images that are continuously patched and scanned, available across LTS Linux (Alpine, Debian, Red Hat, Ubuntu), hardened using STIG/CIS benchmarks (aligned to NIST SP 800‑70), and offered at scale (10,000+ images). They are designed to accelerate FedRAMP/CMMC/SOC 2 readiness and avoid lock‑in by using widely adopted distributions.
Secure Mission Software and Accelerate Your Path to Authorization.
Strengthen compliance readiness, reduce POA&M burden, and safeguard mission-critical software with hardened images, precise vulnerability intelligence, and continuous, audit-aligned evidence.